Best Remote IoT VPC Setup Guide: Secure & Optimized
Why is the future of interconnected devices increasingly reliant on secure, isolated networks? The deployment of a Remote IoT VPC (Virtual Private Cloud) offers a crucial foundation for safeguarding sensitive data, controlling network access, and ensuring the robust operation of a rapidly expanding ecosystem of connected devices.
The proliferation of Internet of Things (IoT) devices from smart home appliances and industrial sensors to autonomous vehicles and medical equipment has created an unprecedented landscape of interconnectedness. This explosion of connectivity, however, comes with significant challenges. Data breaches, unauthorized access, and network vulnerabilities represent persistent threats. Traditional network architectures, often characterized by a flat structure and open accessibility, struggle to effectively manage and secure the massive influx of data generated by these devices. The need for a dedicated, isolated, and highly secure network infrastructure has thus become paramount. Enter the Remote IoT VPC, a strategically designed environment that addresses these crucial concerns.
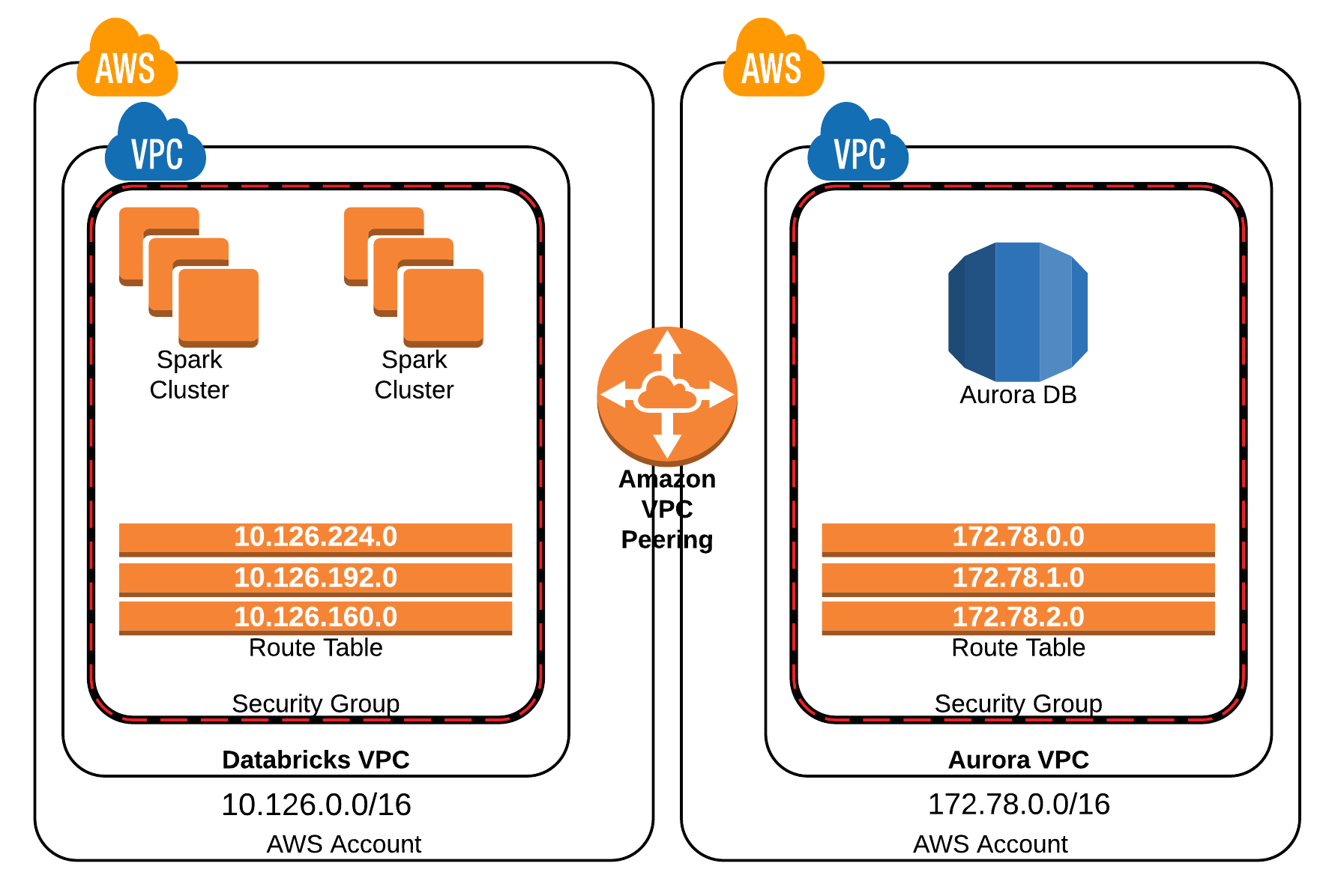
A Remote IoT VPC is, at its core, a private cloud computing environment created within a public cloud infrastructure. It provides a logically isolated network, offering complete control over network resources, access, and security policies. This isolation is critical, as it prevents unauthorized access from the broader internet and isolates IoT devices from each other, mitigating the risk of lateral movement by malicious actors. The architecture of a Remote IoT VPC allows for the creation of multiple subnets, each potentially dedicated to a specific type of IoT device or application. This segmentation further enhances security and allows for granular control over network traffic flow.
The benefits of employing a Remote IoT VPC are multifaceted. Firstly, enhanced security is a primary advantage. By isolating IoT devices and their associated data within a private network, the attack surface is dramatically reduced. Access to the network can be tightly controlled through the use of firewalls, intrusion detection systems, and identity and access management (IAM) policies. Secondly, improved scalability and flexibility are inherent features of cloud-based VPCs. Resources can be easily scaled up or down to meet the changing demands of an expanding IoT deployment. This elasticity eliminates the need for upfront capital investment in hardware and allows for optimized resource utilization. Thirdly, a Remote IoT VPC simplifies network management. Cloud providers offer a range of management tools and services, streamlining tasks such as network monitoring, configuration, and troubleshooting. This reduces the operational burden on IT staff and allows them to focus on other critical priorities.
The use of a Remote IoT VPC is particularly compelling in several key industries. In healthcare, for example, the security of connected medical devices, such as patient monitors and insulin pumps, is of paramount importance. A Remote IoT VPC provides a secure environment for these devices to operate, protecting sensitive patient data and ensuring the reliability of critical medical functions. In manufacturing, the deployment of a Remote IoT VPC enables the secure connection of industrial sensors and equipment, facilitating real-time data analysis, predictive maintenance, and optimized production processes. In the automotive industry, the increasing reliance on connected cars and autonomous driving technologies necessitates a robust and secure network infrastructure. A Remote IoT VPC offers a secure environment for vehicle-to-everything (V2X) communication, software updates, and diagnostic data. In the retail sector, the use of connected point-of-sale (POS) systems, inventory management systems, and customer analytics platforms demands robust security measures. A Remote IoT VPC ensures the secure transmission and storage of sensitive financial and customer data.
Implementing a Remote IoT VPC involves several key steps. The initial step is to select a cloud provider that offers VPC capabilities. Major cloud providers, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), all provide robust VPC services. The next step is to design the VPC architecture, including the creation of subnets, the configuration of security groups and network access control lists (ACLs), and the establishment of network connectivity. This architecture should be tailored to the specific needs of the IoT deployment, considering factors such as the types of devices, the volume of data, and the required levels of security and performance. Once the VPC is designed, the next step is to configure the necessary network services, such as firewalls, intrusion detection systems, and VPN gateways. These services provide crucial security and access control functions. Finally, the IoT devices must be securely connected to the VPC. This may involve the use of virtual private network (VPN) connections, secure shell (SSH) tunnels, or other secure communication protocols. Regular monitoring and maintenance are also essential to ensure the ongoing security and performance of the Remote IoT VPC.
The security considerations for a Remote IoT VPC are extensive. Strong authentication and authorization mechanisms are crucial to ensure that only authorized devices and users can access the network. Multi-factor authentication (MFA) should be implemented wherever possible to enhance security. Data encryption, both in transit and at rest, is essential to protect sensitive data from unauthorized access. Regular vulnerability scanning and penetration testing should be conducted to identify and address any potential security weaknesses. Network segmentation, as mentioned earlier, is a critical component of security. Isolating different types of IoT devices and applications into separate subnets limits the impact of any potential security breaches. Furthermore, robust logging and monitoring are essential to detect and respond to security incidents. Security information and event management (SIEM) systems can be used to analyze log data, identify suspicious activity, and generate alerts. Compliance with relevant industry regulations and security standards, such as those set by the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO), is also crucial.
Performance considerations are equally important. Network latency can significantly impact the performance of IoT applications, particularly those that require real-time data processing or low-latency communication. The choice of cloud provider and the location of the VPC can affect latency. Proximity to the IoT devices is a key factor. The use of content delivery networks (CDNs) can help to optimize the delivery of data to IoT devices located in geographically diverse locations. Network bandwidth is another critical consideration. The VPC infrastructure must be able to handle the volume of data generated by the IoT devices. Scalability is essential to accommodate future growth. Regular monitoring of network performance is essential to identify and address any performance bottlenecks.
Cost optimization is a key factor in the long-term viability of a Remote IoT VPC. Cloud providers offer a variety of pricing models, and it is important to choose the model that best suits the specific needs of the IoT deployment. Factors such as the number of virtual machines, the amount of data storage, and the amount of network bandwidth will impact the overall cost. Using cloud resources efficiently is crucial. Rightsizing virtual machines, optimizing data storage, and monitoring network bandwidth usage can help to reduce costs. Taking advantage of cost-saving features offered by cloud providers, such as reserved instances and spot instances, can also help to optimize costs. Regular cost analysis is essential to ensure that costs are under control and that the Remote IoT VPC is operating in a cost-effective manner.
The future of Remote IoT VPCs is bright. As the number of connected devices continues to grow exponentially, the demand for secure and scalable network infrastructure will only increase. Advancements in cloud computing, artificial intelligence (AI), and machine learning (ML) are further enhancing the capabilities of Remote IoT VPCs. AI and ML can be used to automate security tasks, such as threat detection and incident response. They can also be used to optimize network performance and resource utilization. The integration of edge computing is another significant trend. Edge computing brings processing power closer to the IoT devices, reducing latency and enabling real-time data processing. This is particularly important for applications such as autonomous vehicles and industrial automation. The evolution of 5G networks will also play a significant role in the future of Remote IoT VPCs. 5G offers significantly faster speeds and lower latency than previous generations of mobile networks, enabling new applications and enhancing the performance of existing ones.
The evolution of Remote IoT VPCs is deeply intertwined with broader trends in cloud computing and cybersecurity. The adoption of serverless computing, for example, simplifies application deployment and management, enabling faster innovation and reducing operational costs. Containerization technologies, such as Docker and Kubernetes, further streamline the deployment and management of applications, increasing portability and scalability. The principles of zero-trust security, which assume that no user or device should be trusted by default, are increasingly being applied to Remote IoT VPCs. This involves continuously verifying the identity of users and devices, regardless of their location. This approach significantly reduces the attack surface and improves security. Furthermore, the integration of blockchain technology has the potential to enhance the security and integrity of data within Remote IoT VPCs. Blockchain can be used to create tamper-proof audit trails, ensuring the trustworthiness of data generated by IoT devices. The development of more sophisticated threat intelligence feeds and security analytics tools is also helping to improve the ability to detect and respond to security threats in real time.
In conclusion, the Remote IoT VPC represents a crucial evolution in the landscape of connected devices. It offers a secure, scalable, and manageable network environment that is essential for protecting sensitive data, controlling network access, and enabling the robust operation of the ever-expanding IoT ecosystem. As the number of connected devices continues to grow, and as the sophistication of cyber threats increases, the importance of Remote IoT VPCs will only become more pronounced. Their adoption is not merely a technological choice; it's a strategic imperative for organizations seeking to harness the power of IoT while mitigating its inherent risks. The foresight to embrace these advanced network architectures is a hallmark of forward-thinking organizations prepared to navigate the complexities and capitalize on the opportunities presented by the connected future.
| Category | Details |
|---|---|
| Definition | A logically isolated private cloud computing environment within a public cloud infrastructure, designed to securely connect and manage Internet of Things (IoT) devices. |
| Primary Purpose | To provide a secure and isolated network for IoT devices, protecting sensitive data, controlling access, and improving scalability and manageability. |
| Key Features |
|
| Benefits |
|
| Industries of Application |
|
| Implementation Steps |
|
| Security Considerations |
|
| Performance Considerations |
|
| Cost Optimization |
|
| Future Trends |
|