Fix: Securely Connect Remote IoT VPC AWS Not Working - Guide
Is your remote IoT infrastructure failing to securely connect to your AWS VPC? That seemingly simple sentence can represent a world of frustration for developers and engineers trying to leverage the power of the cloud for their Internet of Things applications. Troubleshooting and resolving connectivity issues in this context demands a thorough understanding of networking, security protocols, and the intricacies of both your remote IoT devices and the AWS ecosystem.
The phrase "securely connect remoteIoT vpc aws not working" encapsulates a common, yet complex, problem. The challenge lies not just in connecting, but in doing so securely. Security, after all, is paramount when dealing with data generated by potentially thousands of remote devices. Further compounding the issue, the term implies the utilization of an AWS Virtual Private Cloud (VPC), which adds another layer of complexity with its custom network configuration. We'll dissect the layers of this issue, helping you to identify the potential bottlenecks and explore the most effective solutions.
Before diving into technical specifics, it's important to acknowledge the multifaceted nature of this problem. It encompasses far more than just a simple IP address conflict or a misconfigured firewall rule. It requires a holistic view of your architecture, including the type of remote IoT devices, the communication protocols they employ, the security mechanisms in place, and the configuration of your AWS VPC. Let's begin by examining each of these key components in more detail, and illustrate a structured troubleshooting approach that will help you pinpoint and resolve the root cause of the connectivity failures.
Many factors can contribute to the scenario of "securely connect remoteIoT vpc aws not working." Let's delve into some key areas that often present challenges. These elements form the foundation for understanding the potential pitfalls.
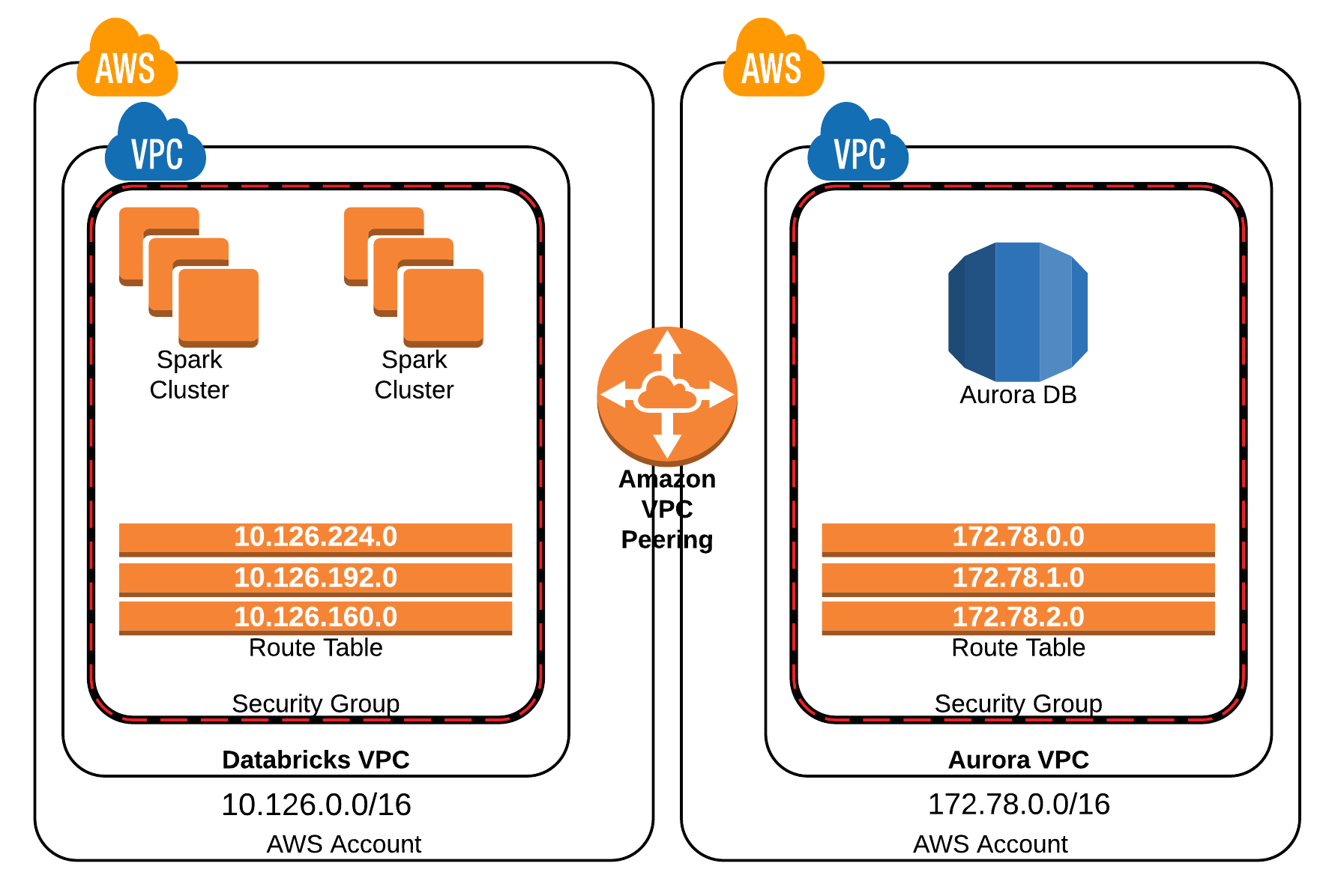
Network Configuration: The network configuration of both your remote IoT devices and your AWS VPC must be meticulously planned. Devices must have a route to connect to the internet to connect back to the VPC.
Security Groups: AWS Security Groups act as virtual firewalls for your resources. Misconfigured security groups are a primary culprit in blocking traffic. Ensure all necessary inbound and outbound traffic is allowed.
Network ACLs: Network Access Control Lists (ACLs) add another layer of firewalling at the subnet level. Like Security Groups, misconfigured ACLs can silently block connectivity.
VPN and Direct Connect: For secure, private connectivity, you might use a Virtual Private Network (VPN) or AWS Direct Connect. Incorrect configuration here can render connections inoperable.
Firewall Rules: Local firewalls on remote devices or intermediary networks can prevent traffic from reaching the VPC. Careful rule configuration is key.
IoT Device Identity and Access Management (IAM): How are your IoT devices authenticated and authorized to access the AWS resources? Improper IAM configuration is a significant security risk.
Device Compatibility: Do your devices support the necessary security protocols and encryption algorithms? Older devices may lack up-to-date support.
Connectivity Testing and Monitoring: Continuous monitoring and thorough testing are crucial for catching problems before they escalate. Use tools to actively check the connections.
Let's begin by breaking down the common issues encountered when attempting to securely connect remote IoT devices to an AWS VPC. First, let's consider the perspective of the remote IoT device itself. These devices can range from simple sensors to complex gateways, each posing unique networking and security considerations. The device must: have a valid IP address that can be routed to your VPC, be able to resolve the DNS names (or know the IP addresses) of the AWS services and your VPCs network interfaces, and have the correct encryption. This means that the device will need an IP address. This address could be public or private. If the address is public, you will need the ability to route traffic from the public internet to your VPC, and then to your devices, which may include the use of NAT. If your devices have a private IP address, then you are relying on a VPN, or a similar technology to connect your devices to the internet.
Now, lets move over to the AWS VPC side. The AWS VPC side presents its own set of challenges. VPCs are logically isolated networks within the AWS cloud. Within your VPC, you need to configure subnets, route tables, security groups, and network access control lists (ACLs) to allow incoming and outgoing traffic. The network configuration is critical to ensure that your IoT devices can communicate with the necessary AWS services and, if necessary, with each other. In addition, when designing the VPC network configuration, remember that security should be a priority. Ensure that you implement the principle of least privilege. That is to say, devices should only be allowed access to what is needed.
Further complicating matters is the use of a VPN or Direct Connect for a secure connection, which may be configured for a public IP or a private IP. This setup adds complexity, requiring specific configurations on both the remote devices and within your VPC to ensure reliable communication. With either option, the configurations must be exact, for example, the VPN must be configured to enable your remote IoT devices to have access to the internet. Similarly, for Direct Connect, the on-premises devices may not be configured to access the internet, and your cloud resources should be configured to connect to the AWS Direct Connect service.
Consider the security protocols and encryption methods employed by your IoT devices and the AWS services they communicate with. TLS/SSL for encrypted communication, and specific security groups and network ACL rules to permit traffic. If the remote devices and AWS services cannot negotiate a secure connection, then the connection is dropped.
The AWS Identity and Access Management (IAM) also is important. This service controls access to AWS resources. Configure proper IAM roles and policies for your IoT devices, restricting access to only the necessary resources. A misconfigured IAM policy might prevent the device from accessing the required resources, even if the network configuration is correct.
Let's explore a typical troubleshooting workflow for this challenging scenario. This is not just a checklist; it's a systematic approach to identify and resolve the root cause of the connectivity problem, it requires patience, but the results are worth it.
1. Verify Basic Connectivity: Begin by establishing baseline connectivity. Can the remote IoT device reach the internet? Use basic tools like `ping` and `traceroute` to test connectivity to external servers or AWS endpoints. This helps to isolate whether the problem lies within the device itself, the local network, or the AWS VPC.
2. Check Device Network Configuration: Inspect the device's network settings. Does it have a valid IP address? Is the subnet mask correct? Is the default gateway pointing to the correct router? Ensure the device can resolve DNS names for AWS services. If the device uses a proxy, confirm the settings are accurate.
3. Examine the AWS VPC Configuration: Review your VPC configuration in the AWS console. Are subnets configured correctly? Are the route tables correctly routing traffic? Are the security groups and network ACLs configured to allow traffic from the device's IP address or subnet?
4. Inspect Security Groups: Review your Security Groups. Ensure that the inbound and outbound rules are configured to allow traffic from the remote device to your VPC. Check both the source and destination ports and protocols. Are the required ports (e.g., 8883 for MQTT, 443 for HTTPS) open?
5. Evaluate Network ACLs: Network ACLs provide an additional layer of security at the subnet level. Review the rules associated with the subnets where your device and AWS resources reside. Ensure the ACLs allow traffic in both directions. ACLs are stateful, meaning they remember which devices initiated a connection.
6. Test VPN or Direct Connect Configuration (If applicable): If you're using a VPN or Direct Connect, review its configuration. Verify the VPN tunnel is up and running. Are the routing tables configured correctly on both sides to forward traffic? Does the Direct Connect connection status show healthy? Are the prefixes advertised from your on-premises network properly configured?
7. Review IAM Roles and Policies: Check the IAM roles assigned to your IoT devices or the AWS resources. Do they have the necessary permissions to access the required AWS services and resources? Ensure the devices are authenticated correctly. You can temporarily increase logging to see what permissions are missing.
8. Analyze Logs: Leverage AWS CloudWatch logs, VPC Flow Logs, and device-specific logs to gain insights into traffic patterns and error messages. Look for blocked connections, authentication failures, or other clues. Enable logging and monitoring for your AWS resources to identify and troubleshoot issues as they arise.
9. Test Communication with Specific Services: Once you have verified connectivity, test communication with specific AWS services like AWS IoT Core, Amazon S3, or Amazon DynamoDB. Use tools like `curl` or dedicated SDKs to send and receive data. Identify where the communication breaks down.
10. Conduct Continuous Monitoring: Implement ongoing monitoring of your network connections, security groups, and device health. Use the dashboards and alerts provided by AWS CloudWatch, enabling you to proactively detect and address connectivity issues before they impact your IoT application.
The journey of securing remote IoT devices and connecting them to your AWS VPC is rarely straightforward. While we have discussed the core issues that are present and the common mistakes made, the process can be demanding. By systematically working through the suggestions and recommendations, you will reduce frustration, and be able to troubleshoot and resolve the issue. The key is to approach each challenge systematically, leverage the resources available to you in the AWS ecosystem, and to pay attention to detail.
Let's examine the crucial component of Device Authentication and Authorization.
Once the network connectivity is in place, it's essential to ensure your IoT devices are authenticated and authorized to access AWS resources. This is where the AWS Identity and Access Management (IAM) service comes into play. Incorrect IAM configuration can lead to access denied errors, even if the network connectivity is functional. Let's break down the common issues and provide the best practices for implementing authentication and authorization.
The first stage to address is the authentication. Authentication confirms the identity of the device. For IoT devices, authentication often involves X.509 certificates. Each device receives a unique certificate from a Certificate Authority (CA), which is then used to identify it to the AWS IoT Core. In the AWS console, you will need to create the necessary certificates to match your devices. It's important to manage the lifecycle of these certificates, including revocation in case of compromise. The second stage is to authorize your devices to access specific AWS resources. This is achieved using IAM policies, which define the permissions of each device, such as the ability to publish data to an IoT topic, read data from an Amazon S3 bucket, or interact with other AWS services. Implement the principle of least privilege by granting only the minimum required permissions to your devices. Regularly audit the permissions granted to your devices to ensure your devices do not have access to more than what is needed.
Another crucial aspect of authentication is the choice of authentication method. X.509 certificates are a common choice for securely authenticating devices to AWS IoT Core. Certificates are often used due to their strong security and the ability to manage and revoke certificates. You must ensure your devices can properly store, manage, and utilize these certificates. However, they can be challenging to manage at scale. Consider other options like SigV4, which uses temporary credentials, which may be more suitable in certain conditions. Use the most secure and efficient mechanism. Another critical aspect is security best practices such as certificate rotation and using strong cryptographic keys, and the ability to update the firmware to add support for newer authentication methods.
Let's delve into how to make your AWS VPC configuration robust and effective. The design choices in your AWS VPC configuration can be the difference between a secure, reliable remote IoT system and a constant source of headaches. From the basic layout, the specific rules, to the advanced settings, each element must be carefully considered to ensure secure connectivity.
First, you must carefully plan the VPC structure. Your VPC architecture begins with the creation of subnets, which are subdivisions of your VPCs address space. You will need to have a private subnet to ensure your remote IoT devices can connect securely. You will also have a public subnet to access the internet and to interact with other AWS services. The size of your subnets will vary, so it is important to factor in your overall IoT fleet's growth. Consider using multiple Availability Zones to improve your application's resilience. Deploy your resources across several zones.
The second aspect to consider is the security group. They act as virtual firewalls, controlling inbound and outbound traffic. Security groups are stateful, meaning they remember which devices initiated a connection. When configuring security groups, follow the principle of least privilege by allowing only the necessary traffic. Use specific inbound and outbound rules to limit the traffic to what is required. Create a detailed set of security group rules. You must allow traffic to the necessary ports.
Now we will consider the Network ACLs which is an additional layer of security at the subnet level. Unlike the security groups, Network ACLs are stateless, so you must configure rules for both inbound and outbound traffic. Consider a more restrictive configuration. Ensure Network ACLs are consistent with the security groups. Both must allow the necessary traffic. For instance, you can implement CIDR blocks. Consider that overlapping CIDR blocks can result in unexpected routing issues.
Next, we will consider the route tables which are used to direct network traffic within your VPC. Route tables define the paths that traffic takes between subnets and the external network. It is important to customize routing to match the location of your devices, especially when using VPNs or Direct Connect. Ensure your route tables are correctly configured. Verify the internet gateway or NAT gateway configuration. Route tables must correctly direct traffic to the internet gateway.
We can not ignore the VPN configuration if your architecture uses a Virtual Private Network (VPN) for secure connectivity between your on-premises network and your VPC, or between remote devices. Proper VPN configuration is vital. Configure the VPN gateway. Configure the VPN tunnel settings, including pre-shared keys and encryption. In addition, we will configure the routing to enable communication between your VPC and your on-premises network. Ensure you have properly configured your VPN and that the tunnel is up. Monitor your VPN connection.
The Direct Connect is a dedicated network connection. For those using AWS Direct Connect to establish a dedicated network connection between your on-premises network and your AWS VPC. It is a reliable and often faster connection. This setup also requires meticulous configuration. Configure a virtual interface. Configure the Border Gateway Protocol (BGP) for routing. You can configure a public or private virtual interface, depending on your requirements. Verify your Direct Connect connection is operational and the configuration matches your network setup. Monitor Direct Connect for connection issues.
When implementing these configurations, remember to regularly review the settings. Network environments often change. Continuous security checks ensure you have not introduced any unintended vulnerabilities. Implement monitoring tools to promptly detect network issues. Proper planning, and vigilant attention to detail are key to your AWS VPC configuration.
In the ever-evolving landscape of IoT, staying ahead requires constant attention to detail and an ongoing commitment to security best practices. We have examined the intricacies of secure remote IoT connections to AWS VPCs. We need to address the continuous monitoring, maintenance, and the best practices.
One of the biggest challenges in IoT is scale. Hundreds, thousands, or potentially millions of devices sending data. As your fleet grows, proactively implementing a proactive approach to monitoring will improve performance and maintain security. Utilize CloudWatch metrics and logs. Set up alerts for network issues, and connectivity problems. Implement continuous monitoring tools.
Regular maintenance is a crucial component of any robust IoT infrastructure. This includes regular patching of devices, updating firmware, and keeping up with the latest security patches. Regularly review and update security group rules, network ACLs, and IAM policies. Regularly test your backups and disaster recovery plans. Create a detailed incident response plan that addresses both security breaches and service disruptions. Regularly perform security audits and penetration tests. Maintain an updated asset inventory. All of these are to make sure that you are maintaining a secure, robust, and efficient IoT infrastructure.
Let's explore some common troubleshooting tips that can help accelerate the process of resolving connection problems.
1. Rule Out the Obvious: Double-check the fundamentals. Verify your internet connection. Confirm the device has a valid IP address and a correct subnet mask. Make sure the device can resolve DNS names.
2. Simplify the Setup: Temporarily remove complex configurations to identify the root cause. For example, to test basic connectivity, temporarily disable firewalls. If you are using a VPN, then temporarily remove it.
3. Use Network Diagnostic Tools: Utilize command-line tools like `ping`, `traceroute`, and `nslookup` to check basic connectivity. `ping` checks if a host is reachable, `traceroute` identifies the path packets take, and `nslookup` tests DNS resolution.
4. Check Port Availability: Use tools like `netstat` or `ss` (on Linux) to check if the necessary ports are open on the device and the AWS side. Ensure that the device and the AWS services are using the correct ports.
5. Review Logs: The logs are the heart of the troubleshooting process. Check the system logs on your devices, the VPC Flow Logs, and the CloudWatch logs. Look for specific error messages.
6. Utilize AWS Tools: Leverage AWS-specific tools to diagnose the problem. The VPC Flow Logs capture detailed network traffic information. AWS CloudTrail logs API calls.
7. Use Packet Capture Tools: Use tools like `tcpdump` (Linux) or Wireshark (Windows/Linux) to capture and analyze network packets. They can help you detect which packets are being sent and received.
8. Consult Documentation and Support: Do not hesitate to refer to AWS documentation, and consult AWS support or community forums. Many common issues have already been addressed, so learning from the others will help.
9. Document Everything: Keep detailed records of all changes and troubleshooting steps. This will help you prevent future issues and aid in quickly resolving future problems.
By adhering to these practices, you'll be well-equipped to solve the challenges. Remember that constant vigilance is the key to creating a robust and secure IoT environment.