Unlocking IoT: The Power Of Remote Access - An Example
Does the pervasive nature of the Internet of Things (IoT) truly hinge on its ability to be controlled from afar? The undeniable truth is that the power and efficiency of remote access are not just features of IoT; they are its lifeblood, the very essence of its utility and scalability. Without the capability to remotely monitor, manage, and manipulate connected devices, the vast promise of IoT would crumble into a tangle of isolated gadgets, incapable of delivering the transformative benefits we increasingly rely upon.
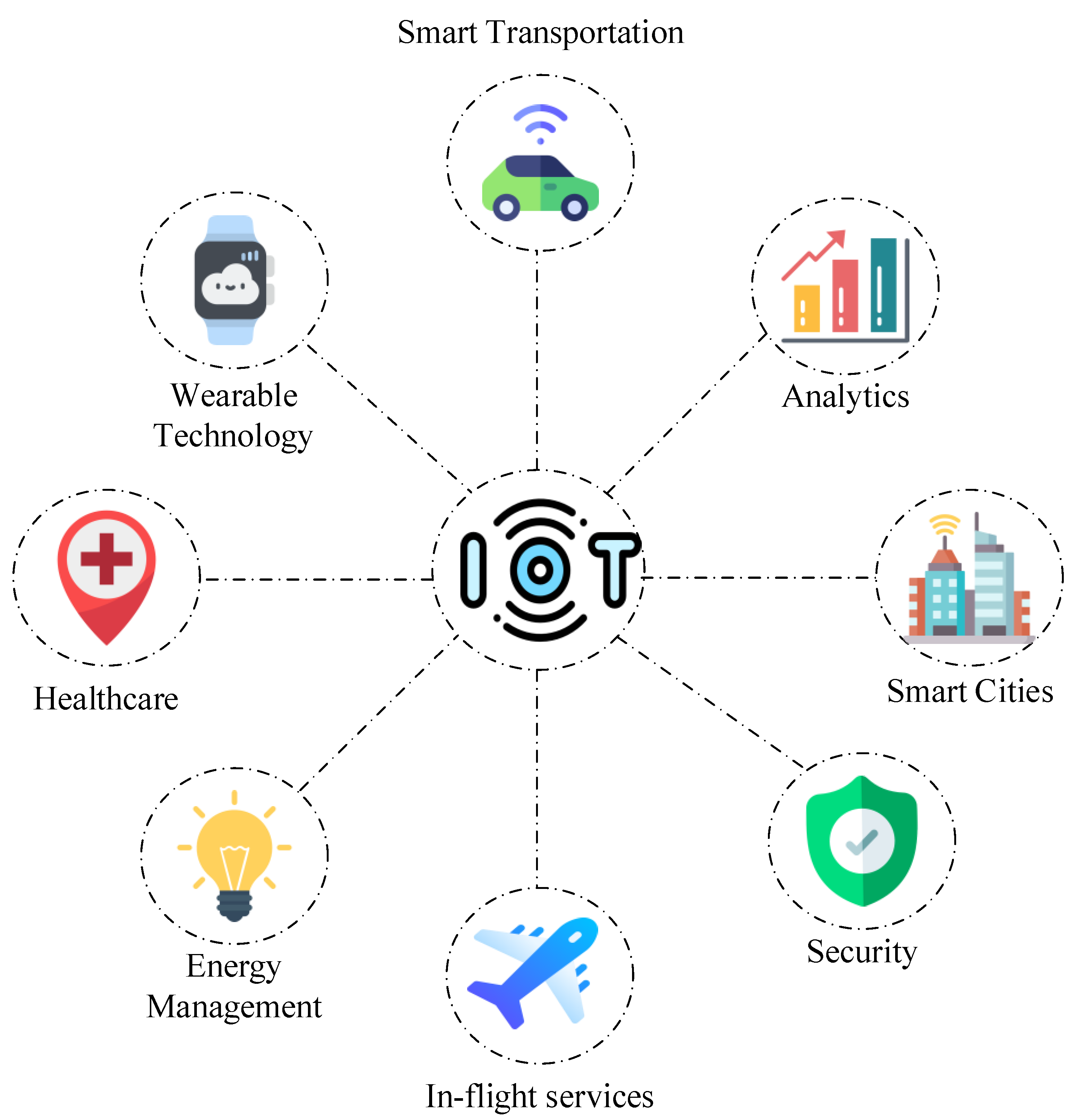
Consider the implications: imagine a smart city where traffic lights cannot be adjusted in real-time to alleviate congestion, or a healthcare system where vital patient data cannot be accessed remotely to provide immediate and critical care. The convenience of remotely controlling your thermostat or unlocking your door pales in comparison to these larger, societal implications. The advantages are vast, spanning sectors from agriculture and manufacturing to healthcare and transportation. The inherent benefits are numerous: optimized resource allocation, proactive maintenance, improved safety, and enhanced operational efficiency. Remote access, in this context, is not simply a convenience; it is a necessity.
Let's delve into a specific, illustrative example: the operation of a modern agricultural operation. Farmers can now employ remote access in several ways. Using sensors distributed throughout a field to monitor soil moisture, temperature, and nutrient levels enables them to remotely control irrigation systems, ensuring optimal crop growth and minimizing water waste. The ability to monitor the condition of machinery and identify potential problems remotely allows for predictive maintenance, reducing downtime and costs. Drones, controlled remotely, survey fields, identifying areas needing attention or displaying signs of pest infestation, then the data obtained can be fed directly into automated systems.
The following table provides a hypothetical but representative illustration of a hypothetical IoT device manufacturer:
| Attribute | Details |
|---|---|
| Name of Company | InnovateConnect Solutions |
| Industry | IoT Device Manufacturing (Smart Home, Industrial Automation) |
| Key Products | Smart thermostats, industrial sensors, remote monitoring systems |
| Core Technology | Wireless Communication Protocols (Wi-Fi, Bluetooth, Cellular), Cloud Computing, Embedded Systems |
| Remote Access Technologies | Secure VPN, Web-based Dashboards, Mobile Applications, API Integration |
| Security Measures | End-to-end encryption, Multi-factor authentication, Regular security audits, Firmware updates |
| Efficiency Gains | Reduced downtime (predictive maintenance), Optimized energy consumption (smart thermostats), Improved resource management (industrial sensors) |
| Challenges | Cybersecurity vulnerabilities, Network latency, Regulatory compliance, User experience |
| Success Metrics | Customer satisfaction, Device uptime, Operational cost reduction, Market share |
| Future Outlook | Expansion of product line, Deeper integration of AI and machine learning, Improved security protocols, Strategic partnerships |
| Reference | Example IoT Company Website (Replace with a relevant website for your research if available) |
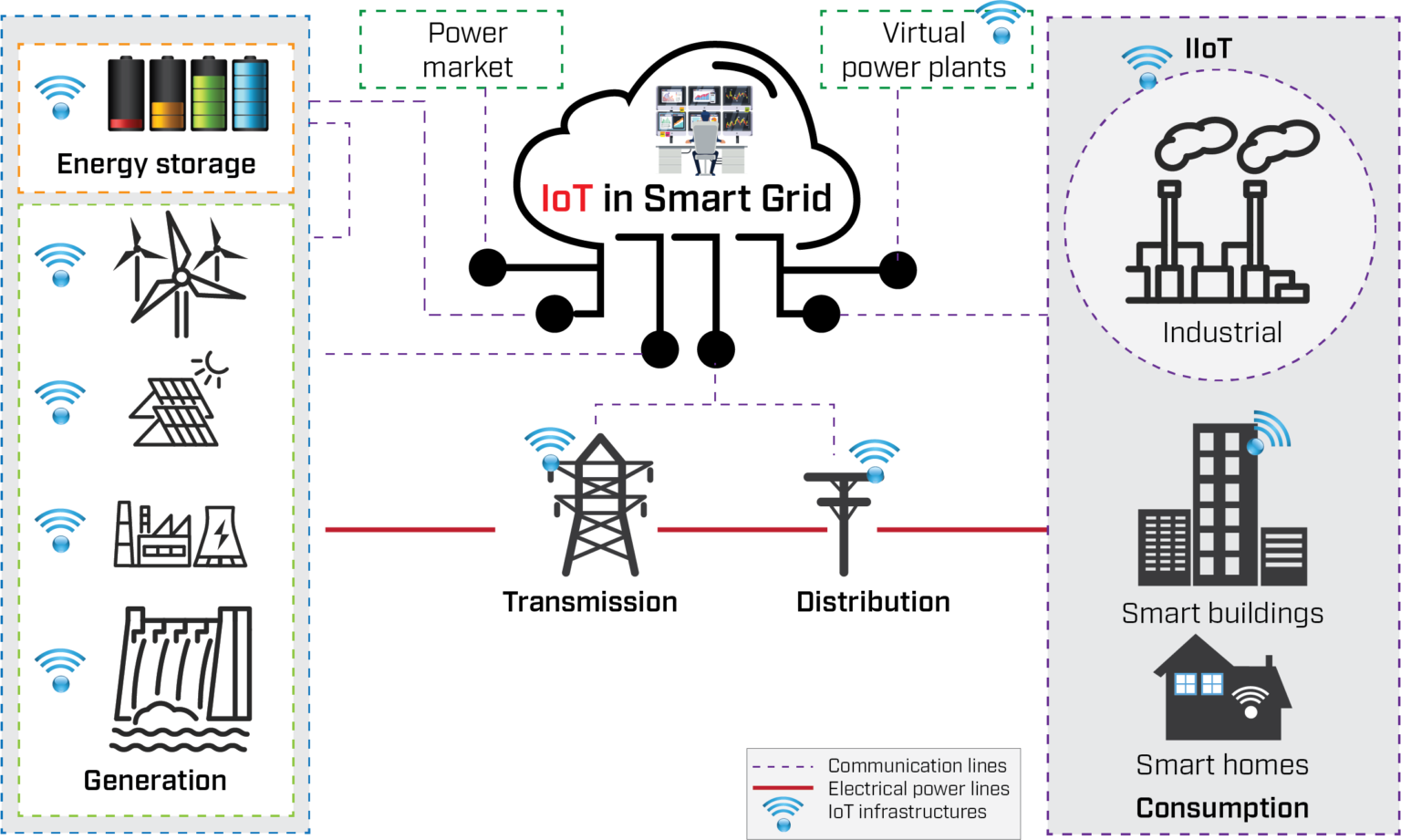
The very fabric of a modern IoT solution is intertwined with the architecture of remote access. It is critical to distinguish between the various access methods and their corresponding levels of sophistication and security. Consider the simple, yet common, smart home application where users employ a mobile app to adjust the temperature of their thermostat or lock their doors. The level of remote access can range from simple commands transmitted over Wi-Fi to more intricate interactions, such as data analysis, automation, and integration with other systems.
In the realm of industrial IoT, the need for robust and secure remote access is even more pronounced. Manufacturing plants deploy sensors and devices to monitor and control every aspect of their production processes. Here, remote access is not simply a convenience but a necessity, enabling engineers to diagnose problems, perform maintenance, and make adjustments to machinery from a central location. This reduces downtime, improves efficiency, and allows for proactive problem-solving. In this setting, however, remote access must be secured with far more stringent protocols than in the smart home setting.
A crucial element of effective remote access lies in selecting appropriate communication protocols. Wi-Fi remains a popular option for devices in close proximity to a router, while cellular networks are increasingly relied upon for devices in remote areas. Low-power wide-area networks (LPWANs) such as LoRaWAN and NB-IoT have emerged as vital options for IoT applications requiring low bandwidth and long battery life. These protocols are essential for long-range communication, enabling things like smart agriculture and monitoring of environmental conditions.
Security is the cornerstone of a secure remote access setup. The vulnerability of IoT devices to cyberattacks has become a well-known concern. Strong passwords, encryption, and multi-factor authentication are all non-negotiable. Regular software updates are crucial to patch security vulnerabilities. The principles of "zero trust" are increasingly important as IoT applications grow. Furthermore, the implementation of robust access control mechanisms is vital for limiting the extent of damage caused by a potential breach.
Consider the use of Virtual Private Networks (VPNs). VPNs create an encrypted tunnel, securely transmitting data. This safeguards sensitive information from interception. Another vital technique is employing a secure, web-based dashboard. This allows users to monitor and control devices from any web-enabled device. These dashboards must have secure logins, authentication, and encryption protocols to prevent unauthorized access. Mobile applications, too, should also incorporate security features such as encryption, device authentication, and regular security updates.
The impact of cloud computing is essential to remote access. Cloud platforms provide the infrastructure needed to store, manage, and analyze data generated by IoT devices. This allows users to access and interpret data from anywhere in the world with an internet connection. This makes remote management far more efficient and scalable. Cloud-based analytics further enable predictive maintenance and anomaly detection, vastly improving operational efficiency.
The convergence of Artificial Intelligence (AI) and Machine Learning (ML) is further enhancing remote access capabilities. AI-powered systems can analyze vast amounts of data generated by IoT devices, identifying patterns, predicting potential problems, and automating responses. This allows for more intelligent and proactive remote management, optimizing performance and reducing downtime. For example, in a manufacturing setting, ML algorithms can analyze sensor data to predict equipment failures, allowing for preventative maintenance and avoiding costly disruptions.
Edge computing is a critical factor in improving the efficiency of remote access. Edge computing involves processing data closer to the source, rather than relying solely on a centralized cloud server. This reduces latency, improving responsiveness and enabling real-time decision-making. This is particularly useful in applications where speed is critical, such as autonomous vehicles or industrial automation. Edge computing also provides greater data security and privacy, as sensitive data can be processed locally, reducing the risk of transmission.
The challenge for IoT developers lies in navigating a complex regulatory landscape. The emergence of new standards and protocols, such as the Matter smart home standard, is driving the standardization of remote access across different devices. Regulations such as the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR) impact how data is collected, stored, and used, affecting remote access protocols.
The implications of remote access extend far beyond individual devices and applications. Consider the rise of smart cities: networked traffic management systems, intelligent waste management systems, and remote control of utilities require robust, secure remote access to operate effectively. Remote access is equally important in healthcare. Remote patient monitoring systems allow healthcare providers to collect vital signs and other health data from patients remotely, allowing for better care and reducing hospital readmissions. Agriculture, too, benefits from remote monitoring.
The future of remote access in IoT is bright, with ongoing developments focused on enhanced security, improved connectivity, and increased intelligence. The advent of 5G technology will facilitate faster data transfer rates and lower latency, enabling even more sophisticated and responsive remote access capabilities. Furthermore, the continued integration of AI and machine learning will lead to more automated and intelligent remote management systems. The trend toward edge computing will accelerate, further improving data security, efficiency, and real-time responsiveness.
The role of remote access will become more integral to our lives, shaping how we interact with our environment and each other. The success of IoT in transforming the world will be measured by the efficiency and security with which we can remotely access and control the connected devices that define the 21st century.
Consider the following scenario: A logistics company employs a fleet of remotely monitored and controlled trucks. Sensors track the vehicle's location, fuel consumption, and engine performance. Through a central dashboard, fleet managers can monitor vehicle health, optimizing routes in real-time to avoid traffic and reduce fuel consumption. When a problem arises, such as a tire pressure issue, the driver receives an alert instantly. This immediate, remote access to data reduces downtime, improves efficiency, and enhances the safety and reliability of operations.
As the IoT ecosystem grows, the need for a holistic approach to remote access becomes increasingly important. This means addressing not only the technical challenges of security and connectivity but also the human factors, such as user experience, training, and usability. The user experience of remote access systems must be intuitive and easy to use. Complex systems can be simplified with the incorporation of user-friendly interfaces, making remote management accessible to a wider range of users.
The benefits of remote access are clear, but the potential for misuse remains. Therefore, robust security measures, compliance with relevant regulations, and adherence to ethical guidelines are vital. The developers, manufacturers, and operators of IoT devices must assume responsibility for securing their systems. This protects against cyber threats and ensures responsible and ethical data handling. Transparency with users regarding data collection, use, and security protocols is crucial.
The discussion of remote access in IoT reveals a profound interconnection between technology, security, and human life. It is not simply a technological problem, but a societal one. It calls for collaboration among technologists, policymakers, and end users. Only through such collaboration can we truly unlock the transformative potential of the Internet of Things, while mitigating risks and maximizing benefits. The future hinges on our ability to navigate this complex, interconnected world with intelligence, vigilance, and a commitment to responsible innovation. The power of remote access is now, and the implications will continue to evolve.