Remote VNC Access: Securely Connect Through SSH & Firewall
Can you truly access your home computer, nestled securely behind a firewall, from anywhere in the world? The answer lies in understanding the principles of network tunneling, SSH port forwarding, and the careful configuration of your home network. This approach, although requiring some technical understanding, offers a secure and reliable method to bypass the restrictions imposed by firewalls and routers, allowing you to remotely control your machine as if you were sitting right in front of it.
The challenge is a common one: you have a Linux computer at home, connected to the internet through a service like Comcast, which, by default, blocks incoming connections. You want to access this computer remotely, perhaps to work on files, manage your system, or simply have access to your home network resources. Direct access, by entering the public IP address, is impossible because the firewall is actively preventing it. However, all is not lost. There are several methods to achieve this goal, each with its own complexities and nuances. The most effective and secure solution generally revolves around establishing a secure tunnel through an SSH server.
Before diving into the technical aspects, its crucial to clarify the setup. In this scenario, you have three main components: your local computer (the one you're using to connect), a remote computer (the one you want to access, behind the firewall), and a third computer (the "SSH server," which sits between the other two). Ideally, the SSH server should be on a network that you control, often your home network. The SSH server acts as a bridge, forwarding traffic between your local machine and the remote machine.
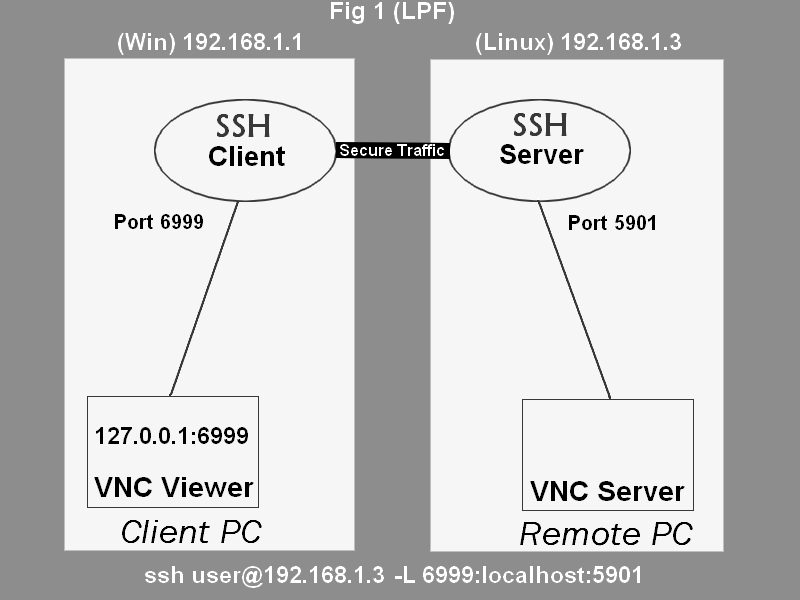
The core of the solution lies in the principle of Secure Shell (SSH) tunneling. SSH, a secure network protocol, can be used not only for remote command-line access but also to forward network ports. This means that you can configure your local computer to connect to the SSH server and then, through the SSH server, connect to the remote computer. All traffic passing through the tunnel is encrypted, ensuring security. This effectively bypasses the firewall because the initial connection is made to the SSH server on a standard SSH port (typically port 22), which is often allowed through the firewall.
The first step is to ensure that the SSH server is properly configured. On the SSH server (the computer that you can control and that sits between your local and remote machines), you need to edit the SSH configuration file, typically located at /etc/ssh/sshd_config. In this file, you must ensure that the line GatewayPorts yes is present. This setting allows the SSH server to forward ports in a way thats necessary for remote access. If you had to add or modify this line, you will then need to restart the SSH service (e.g., using the command sudo systemctl restart sshd on a systemd-based Linux distribution or sudo service ssh restart on other systems).
Once the SSH server is configured, youll need to set up port forwarding on your local machine. The exact command will depend on your specific setup, but a typical example would look something like this in a terminal window:
ssh -L 5900:remote_computer_private_ip:5900 user@ssh_server_public_ipLet's break down this command:
ssh: This initiates an SSH connection.-L 5900:remote_computer_private_ip:5900: This is the port forwarding option. It tells SSH to forward local port 5900 (on your local machine) to port 5900 on the remote computer, effectively creating a tunnel. Replaceremote_computer_private_ipwith the private IP address of your remote computer on your internal network (e.g., 192.168.1.100).user@ssh_server_public_ip: This specifies the username and public IP address or domain name of the SSH server.
After running this command and authenticating with your SSH server credentials, a secure tunnel will be established. You can then use a VNC viewer on your local computer to connect to localhost:5900. This will effectively connect you to your remote computer's desktop. If the remote computer uses a different display number than 0, you will need to adjust the port number in both the SSH command and the VNC client (e.g., use 5901 for display 1, 5902 for display 2, and so on).
Another crucial aspect is the functioning of the VNC server on the remote machine. You must have a VNC server (like TightVNC or RealVNC) installed and running on the remote Linux computer. The VNC server must be configured to listen on a specific port (usually 5900 for display 0) and to allow connections. Ensure that the VNC server starts automatically on boot, so you can access your remote machine even after a restart. On the remote machine, verify that the VNC service is up and running.
One additional factor to consider is the public IP address of your home network. If the IP address assigned by your internet service provider (ISP) changes frequently (which is common with dynamic IP addresses), its wise to use a dynamic DNS (DDNS) service. DDNS services allow you to associate a domain name (like yourhome.dyndns.org) with your dynamically changing IP address. You would need to register with a DDNS provider, set up the DDNS client in your router's configuration (most routers support this), and then use the dynamic domain name in your SSH command.
In cases where you need web server access to remote devices behind a firewall, SSH port forwarding remains the answer. By default, the firewall is turned on and SSH is blocked. You will need to add SSH to the allowed services if needed. On the administrator system, an SSH connection will need to be established to the remote system. Then from the terminal, run the SSH command. A secure connection to a remote desktop can be achieved using open-source VNC or TightVNC software. Notably, this method avoids additional open ports beyond the SSH port on the remote server/router/firewall, which is generally considered a good security practice.
Firewalls, as the name implies, are designed to prevent unauthorized network access. The tunnel effectively bypasses these restrictions, because the initial connection is made to a service (SSH) that is allowed through the firewall. While SSH tunneling is often used for remote access, it's important to understand the implications, including the potential risks. Also, it may get you in trouble with the administrator of the remote network if you do not own the remote network.
Beyond the basic setup, consider the following advanced techniques:
- Multiplexing: You can enhance the speed and efficiency of your SSH connection by enabling connection multiplexing. This allows multiple SSH sessions to share a single TCP connection, reducing overhead. Use the
-Mand-Soptions in your SSH command to enable and configure this. - Key-based authentication: Instead of using passwords, use SSH keys. This is significantly more secure and convenient. Generate a key pair on your local machine and add the public key to the authorized keys file on the SSH server.
- Firewall configuration: If you have control over the firewall on the SSH server, configure it to restrict access to the SSH port to specific IP addresses or networks. This enhances security by limiting the potential attack surface.
- Regular security audits: Regularly review your system logs and security configurations for any vulnerabilities. Keep your software and system updated with the latest security patches.
Troubleshooting Tips:
- Connection refused: This usually indicates a problem with the VNC server (is it running?), firewall (is port 5900 open locally and remotely?), or incorrect port forwarding settings in your SSH command.
- "No route to host": This likely means the remote computer's private IP address is incorrect, or the SSH server cannot reach the remote computer on the private network.
- SSH connection timeout: This could be a network issue, an incorrect SSH server address, or firewall restrictions.
In summary, the process involves setting up an SSH server on a machine accessible from the internet, enabling port forwarding through SSH, and finally using a VNC client to connect to your remote desktop. Remember to consider security best practices. SSH tunneling, when implemented correctly, provides a robust and secure way to establish VNC connections to computers behind firewalls. With a little technical know-how, you can easily access your home computer from anywhere.
Here is a table with related information:
| Component | Description | Configuration Steps | Troubleshooting Tips |
|---|---|---|---|
| Your Computer (Local) | The machine you are using to initiate the remote connection. | Install VNC Viewer, Configure SSH port forwarding | Check network connectivity, Verify VNC Viewer settings. |
| SSH Server | A server that is accessible from the internet. | Install and configure SSH, Ensure GatewayPorts is set to yes in /etc/ssh/sshd_config. | Verify SSH service status, Check firewall rules. |
| Remote Computer | The machine you want to connect to, behind a firewall. | Install and configure a VNC server. | Verify VNC server status, Check internal network connectivity. |
| Firewall/Router | Network device that blocks incoming traffic | Configure SSH Port Forwarding. | Verify SSH port is open, Check for other network conflicts. |
| Dynamic DNS | Used when the public IP address changes frequently. | Register with a DDNS provider, set up DDNS in your router | Ensure the DDNS service is updating correctly. |