SSH Into Raspberry Pi With Firewall: A Beginner's Guide
Are you finding yourself stymied by your Raspberry Pis firewall when trying to access it remotely? Successfully establishing a secure SSH connection to your Raspberry Pi, even with a firewall in place, is not just possible but essential for remote administration and project management, offering a potent blend of security and accessibility. It's a common challenge, but with the right understanding and configuration, you can unlock secure remote access.
The core of the issue lies in the intersection of network security and the need for remote access. A firewall, by its very definition, acts as a barrier, controlling incoming and outgoing network traffic. SSH (Secure Shell), on the other hand, is a protocol designed to provide a secure way to connect to a remote server, like your Raspberry Pi, for command-line access and file transfer. The key is to configure both the firewall and SSH to work in harmony, allowing authorized connections while blocking unauthorized ones.
The first step in achieving this delicate balance is understanding your network setup and the role of your firewall. Most home networks utilize a router that acts as a hardware firewall. Within your Raspberry Pi itself, you likely have a software firewall active, perhaps configured using `iptables` or `ufw` (Uncomplicated Firewall). Identifying the specifics of your setup is crucial. Determine the IP address of your Raspberry Pi on your local network and the public IP address of your router. This information forms the foundation for the subsequent configuration steps.
Assuming you're using `ufw` on your Raspberry Pi, a common and user-friendly choice, the process begins with enabling SSH and allowing traffic on port 22 (the default SSH port). However, blindly opening port 22 to the world is a security risk. Thus, we'll implement additional security measures. Before enabling SSH, it is a good practice to update and upgrade the system. Run the following commands on your Raspberry Pi:
sudo apt updatesudo apt upgrade
Then, to enable SSH and allow connections, the following `ufw` commands are essential:
sudo ufw allow sshsudo ufw enable
The `sudo ufw allow ssh` command essentially creates a rule to allow incoming SSH traffic. The `sudo ufw enable` command then activates the firewall, applying your configured rules. You can check the status of `ufw` with `sudo ufw status`. You should see that SSH (port 22) is allowed.
On your router's firewall, you'll need to configure port forwarding. This process varies depending on your router model, but generally involves logging into your router's administration panel (usually through a web browser using an IP address like 192.168.1.1 or 192.168.0.1). Look for a section labeled "Port Forwarding," "Virtual Servers," or similar. Here, you'll create a rule to forward traffic on port 22 (or the port you choose for SSH, more on this later) to the internal IP address of your Raspberry Pi. You'll also need to specify the protocol (TCP). Remember to consult your router's manual for specific instructions, since each router has a different user interface.
Crucially, before implementing port forwarding, it's important to consider security implications. Opening ports on your router makes your Raspberry Pi accessible from the internet, increasing the risk of unauthorized access. Therefore, its not enough to simply enable SSH and forward ports. We will implement additional security measures:
One of the most effective measures is to change the default SSH port. This practice, known as "security through obscurity," won't stop a determined attacker, but it will reduce the number of automated attacks. To change the SSH port, edit the SSH configuration file:
sudo nano /etc/ssh/sshd_configFind the line that starts with `Port 22` and change `22` to a different port number, such as `2222` (or any other port above 1024 that isn't already in use). Make sure to choose a port number that is not used by other services on your Pi or network. Then, save the file and restart the SSH service:
sudo systemctl restart sshdAfter changing the SSH port, youll need to update your firewall rules on both your Raspberry Pi and your router to reflect the new port number. On your Raspberry Pi (using `ufw`), allow the new port:
sudo ufw allow 2222On your router, adjust the port forwarding rule to forward traffic from the new external port to the Raspberry Pi's internal IP address on the new port (2222 in this example).
Another important security measure is disabling password-based authentication and using SSH keys instead. SSH keys provide a more secure way to authenticate because they use cryptography, which is much harder to crack than a password. The process involves generating a key pair (a private key and a public key) on your local machine and copying the public key to your Raspberry Pi.
Generate an SSH key pair on your local machine (e.g., your laptop or desktop) using the `ssh-keygen` command:
ssh-keygen -t rsa -b 4096This command will create a new key pair using the RSA algorithm and a key size of 4096 bits (a strong level of security). You'll be prompted to enter a passphrase, which is highly recommended for added security. This passphrase will protect your private key.
Then, copy the public key (usually found in `~/.ssh/id_rsa.pub`) to your Raspberry Pi using the `ssh-copy-id` command. Replace `pi@your_raspberry_pi_ip` with the correct username and IP address or hostname of your Raspberry Pi:
ssh-copy-id -i ~/.ssh/id_rsa.pub pi@your_raspberry_pi_ipYou'll be prompted for your Raspberry Pi password the first time. After successful authentication, the public key is added to the `~/.ssh/authorized_keys` file on your Raspberry Pi, allowing key-based authentication.
Once the public key is copied, test the connection to ensure that it works. Then, on your Raspberry Pi, edit the SSH configuration file again:
sudo nano /etc/ssh/sshd_configFind the following lines and modify them to disable password authentication and enable key authentication:
PasswordAuthentication yes# Change toPasswordAuthentication noPubkeyAuthentication yes
If you changed the SSH port earlier, also remember to include this detail in the SSH configuration for your local machine when you connect to your Raspberry Pi using SSH keys.
Finally, restart the SSH service for the changes to take effect:
sudo systemctl restart sshdOne of the most vital tools available for securing your SSH connections, especially when dealing with firewalls and remote access, is `fail2ban`. `Fail2ban` is an intrusion prevention software framework that protects computer servers from brute-force attacks. It monitors log files (like the SSH log) for failed login attempts and, based on configurable rules, bans the offending IP addresses for a specific period. This helps to protect your Raspberry Pi from automated attempts to crack your SSH credentials.
To install `fail2ban` on your Raspberry Pi:
sudo apt updatesudo apt install fail2ban
After installation, `fail2ban` is typically configured to monitor SSH attempts by default. However, it's good practice to review the configuration file (located at `/etc/fail2ban/jail.local`) to ensure it is set up to your preferences. You can create this file by copying the default configuration file (`/etc/fail2ban/jail.conf`). First, copy the file:
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.localThen, edit the `jail.local` file using your preferred text editor (e.g., `nano` or `vim`):
sudo nano /etc/fail2ban/jail.localWithin this file, you can configure several settings. For instance, you can set the ban time (how long an IP address is blocked), the maximum retry attempts before a ban, and the actions `fail2ban` should take. Locate the section related to `[sshd]` and modify its settings as needed. For example, increase the `bantime` or reduce the `maxretry` values for improved security.
After making your changes, restart the `fail2ban` service:
sudo systemctl restart fail2banThis action helps to ensure that `fail2ban` is up-to-date and working properly.
Another approach for securing your Raspberry Pi is to use a VPN (Virtual Private Network). A VPN creates an encrypted connection between your local machine and your Raspberry Pi's network. By connecting to your Raspberry Pi via a VPN, you can essentially bypass the need to directly open ports on your router. All traffic is encrypted, adding another layer of security. While requiring an initial setup, using a VPN can provide greater security than direct SSH access.
Setting up a VPN on your Raspberry Pi typically involves installing and configuring VPN server software, such as OpenVPN or WireGuard. The process usually includes generating keys and certificates, configuring the server, and setting up client software on your local machine. Once the VPN is established, you can SSH into your Raspberry Pi using its local IP address within the VPN network, effectively bypassing the firewall restrictions and securing the traffic.
Before beginning, decide which VPN software to use. OpenVPN is widely used and well-documented. WireGuard, a newer option, often provides better performance and simpler configurations. You will need to install the relevant packages on your Raspberry Pi and your client machines. For OpenVPN, this includes the `openvpn` package. For WireGuard, it includes the `wireguard` package.
For this example, let's assume you're using OpenVPN. On your Raspberry Pi (acting as the VPN server), you'll typically install the `openvpn` package, and then configure the server settings. This often involves generating keys and certificates to ensure secure connections. There are several good tutorials that explain OpenVPN setup in detail. You will then need to configure your router to forward the VPN traffic.
Configuring OpenVPN and WireGuard require specific attention to detail and understanding of network concepts such as port forwarding, IP addressing, and routing. Many tutorials available online provide step-by-step instructions, but the exact steps depend on the VPN software you choose and your specific network setup.
Note: Using a VPN requires an understanding of networking concepts such as port forwarding, IP addressing, and routing. There are multiple good tutorials available online providing step-by-step instructions. Your router will need to forward incoming traffic for the VPN port (usually UDP 1194 for OpenVPN) to your Raspberry Pis internal IP address.
Using `iptables` directly offers the most flexibility, as it allows you to fine-tune the firewall rules. If you're comfortable with the command line, `iptables` provides the most control. But, it can be complex. The `iptables` tool allows you to inspect and modify the firewall rules, and these rules dictate how network traffic is handled. Each rule specifies a matching condition (such as the source IP address, destination port, or protocol) and an action to take if the condition is met (such as accepting, rejecting, or dropping the packet).
To get started, list the current `iptables` rules by running:
sudo iptables -LThis will show you the current chain of rules, which includes `INPUT`, `OUTPUT`, and `FORWARD` chains. The `INPUT` chain controls incoming traffic to the Raspberry Pi itself. The `OUTPUT` chain controls outgoing traffic. The `FORWARD` chain is used for traffic that passes through the Pi (e.g., if it acts as a router). Modifying the `INPUT` chain is where you'll create rules to allow SSH connections while blocking other traffic.
To allow SSH traffic on port 22 (or your chosen port) using `iptables`, create a rule using:
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPTThis command adds a rule to the `INPUT` chain (`-A INPUT`). It specifies the protocol (`-p tcp`), the destination port (`--dport 22`), and the action (`-j ACCEPT`), which accepts the traffic. To reject all other incoming traffic, add this rule to reject other traffic:
sudo iptables -A INPUT -j REJECTThis command rejects all incoming traffic that does not match the previous rules.
Important: When using `iptables`, the order of rules matters. The rules are processed in the order they appear in the chain. If you accidentally create a rule that blocks SSH before the rule that allows it, you will be locked out of your Raspberry Pi. Save your `iptables` rules regularly with the command `sudo iptables-save > /etc/iptables/rules.v4` or `sudo iptables-save > /etc/iptables/rules.v6`. Then, when you reboot the system, it will reload the configurations.
Also, using `iptables` requires caution, because misconfiguration can lock you out of your Raspberry Pi. To recover from lockout due to firewall misconfiguration with iptables, consider setting up a serial console connection. This allows you to access the Pi even if network access is blocked. Alternatively, you could configure your router to allow specific IP addresses for SSH, for enhanced security.
The use of a reverse proxy is another advanced, yet powerful, method of securing your Raspberry Pi. A reverse proxy sits in front of your Raspberry Pi and acts as an intermediary. This approach provides an extra layer of security by hiding the internal structure of your network from the outside world. Instead of directly exposing your Raspberry Pi to the internet, you expose the reverse proxy server. All incoming traffic is directed to the proxy. The proxy then forwards the authenticated traffic to your Raspberry Pi.
One common reverse proxy is Nginx, known for its performance and versatility. Nginx can handle SSL encryption, act as a load balancer, and provide caching, further enhancing security and performance. To use Nginx as a reverse proxy for SSH, you would configure Nginx to listen on port 443 (or another port), handle SSL/TLS encryption (encrypting all traffic between the client and the proxy), and forward authenticated SSH traffic to your Raspberry Pi. The configuration is typically done using directives within Nginxs configuration files, which can be a bit complex to set up, but provide a considerable level of control.
The advantages of using a reverse proxy include:
- Enhanced Security: The reverse proxy acts as a shield, hiding the internal structure of your network and Raspberry Pi.
- SSL Encryption: The reverse proxy can handle SSL/TLS encryption, protecting your SSH traffic.
- Load Balancing: If you have multiple Raspberry Pis or need to handle a large number of connections, Nginx can distribute the traffic.
Considerations for Reverse Proxy Implementation:
- Complexity: Setting up and configuring a reverse proxy, especially for SSL encryption, can be more complex than other methods.
- Performance Overhead: The reverse proxy can introduce a slight performance overhead due to the additional processing.
- Resource Requirements: The reverse proxy server requires resources (CPU, memory) to operate.
Each of these approaches presents a slightly different trade-off between security, complexity, and ease of use. Choosing the right method depends on your specific needs and technical expertise. Remember to start with the basics, configure your firewall properly, use SSH keys, and implement security best practices.
Once you've successfully configured SSH access through your firewall, it's time to connect. On your local machine, open a terminal (Linux/macOS) or use an SSH client like PuTTY (Windows). Use the following command to connect to your Raspberry Pi, replacing the placeholders with your actual details:
ssh pi@your_raspberry_pi_ip -p 2222Where:
- `pi` is the username (usually the default on Raspberry Pi OS).
- `your_raspberry_pi_ip` is the IP address of your Raspberry Pi (the public IP address if you are connecting from outside your local network or the local IP address if you are on the same network).
- `-p 2222` specifies the port number (if you have changed from the default port 22).
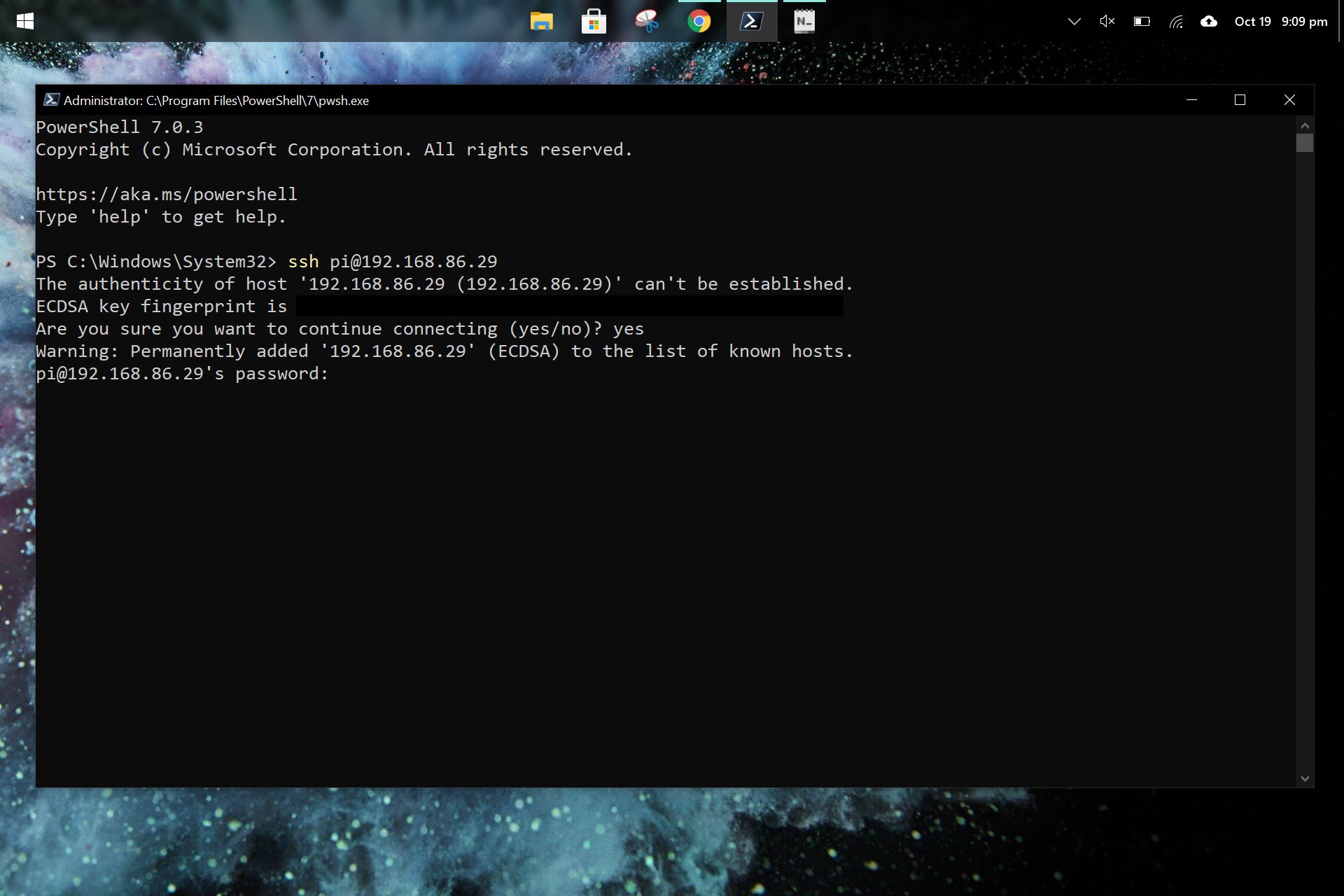
If you're connecting for the first time, you may be prompted to accept the host key. Type `yes` to accept and continue. Then, enter your password (if you're not using SSH keys). After a successful authentication, you will be logged into your Raspberry Pi and can begin working on your project.
Troubleshooting common issues:
If you encounter issues during the process, these tips might help:
Connection Refused: Check that the SSH service is running on your Raspberry Pi (`sudo systemctl status sshd`). Verify that the firewall allows SSH connections on the correct port. Also, make sure that the port forwarding on your router is correctly configured.
Timeout: Ensure that the IP address and port number are correct. Check your firewall settings, both on the Raspberry Pi and on your router. Your internet connection might have problems.
Authentication Failed: Verify that you're using the correct username and password (or your SSH key is set up correctly). Double-check the SSH configuration files on the Raspberry Pi for any errors.
"Host key verification failed": If you are connecting for the first time, or have reinstalled the operating system, you will sometimes need to accept a "host key" when you first connect. Make sure that this matches the information shown on the Raspberry Pi console, and that you trust this key before accepting it.
Remember: Always create a backup before making any changes to your firewall or network configuration. The best approach is to start slowly, by allowing only SSH and then ensuring that your port-forwarding and/or VPN is correctly set up. It is much easier to lock yourself out of your Raspberry Pi, if you accidentally misconfigure your network settings. Having backups, and good documentation, allows you to recover quickly.
Securing SSH access through a firewall is not merely a technical exercise; it's a critical practice for anyone working with a Raspberry Pi remotely. By understanding the core principles of firewalls, SSH, and network security, you can establish a secure and accessible connection to your device. Remember to prioritize security best practices such as using SSH keys, changing the default port, and employing `fail2ban` to protect your Raspberry Pi. The ability to securely connect is essential for remote administration, software development, and the successful deployment of a wide range of projects, from home automation to robotics.