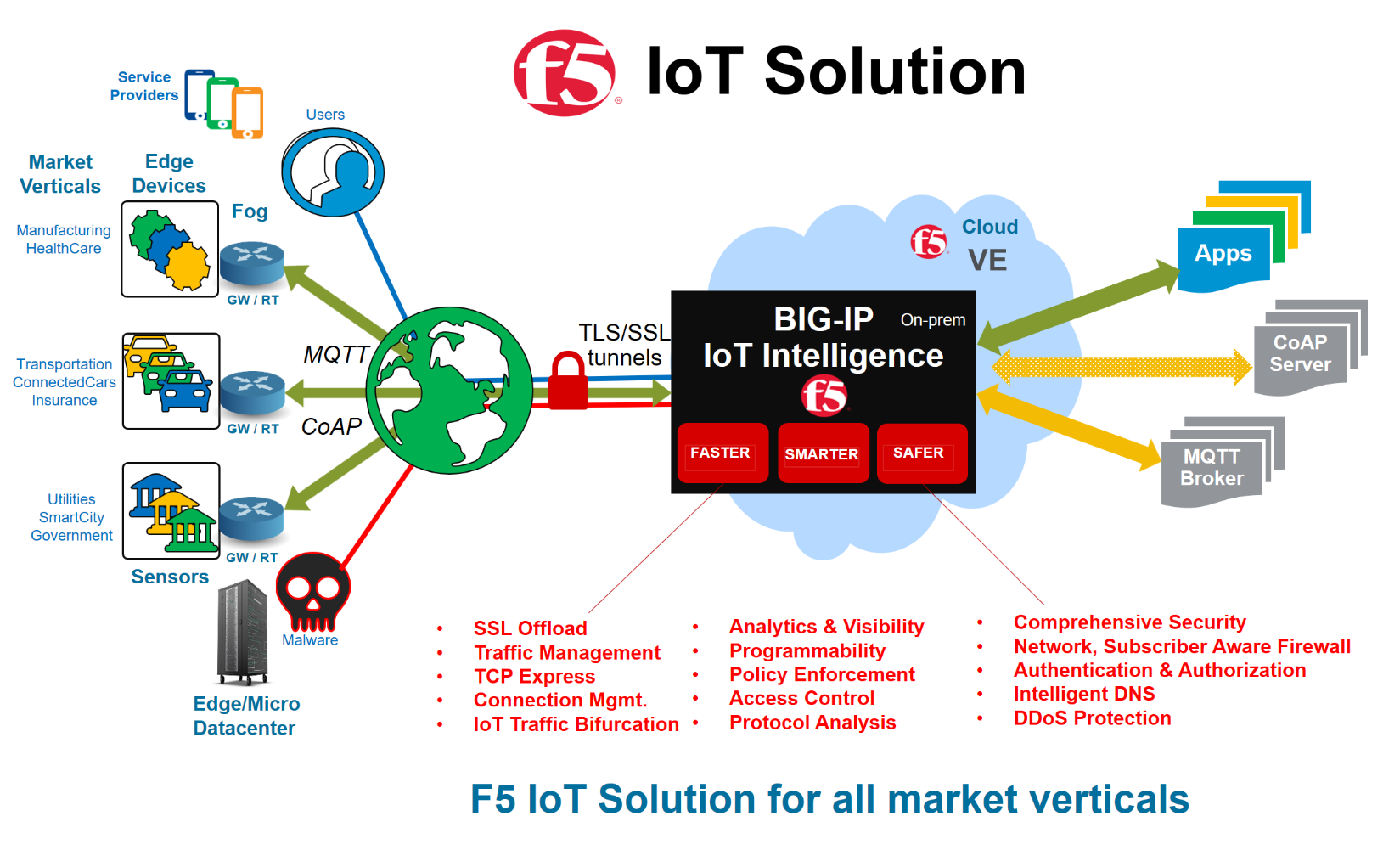
Protect Your IoT: Firewall Devices & Security Guide
Are you concerned about the security of your smart home devices? The proliferation of Internet of Things (IoT) devices has created a landscape ripe for cyberattacks, making robust firewall protection more critical than ever before.
The interconnected world we inhabit, where refrigerators order groceries and thermostats adjust temperatures remotely, is built upon the silent operation of IoT devices. These devices, from smart TVs to connected security cameras, bring convenience and efficiency to our lives. However, this connectivity also introduces significant vulnerabilities. Each device, often with weak or default security settings, presents a potential entry point for malicious actors. Exploiting these vulnerabilities can lead to data breaches, privacy violations, and even physical harm. The inherent complexity of managing a multitude of connected devices, coupled with a lack of user awareness, further exacerbates the risks.
The concept of a "firewall" in the context of IoT devices is fundamentally about creating a barrier between the devices and the outside world. It's a gatekeeper, meticulously inspecting all incoming and outgoing network traffic and allowing only authorized communication. This is particularly important in today's digital age, where cyber threats are constantly evolving. Consider the scenario of a smart thermostat being compromised; an attacker could manipulate the temperature, potentially leading to increased energy bills or even damage to the HVAC system. Or, imagine a hacked smart security camera; the compromised footage could be used for extortion or other malicious purposes. Therefore, understanding how to secure these devices is paramount.
Traditional firewalls, designed for computers and networks, often struggle to adapt to the unique characteristics of IoT devices. IoT devices are typically resource-constrained, meaning they have limited processing power and memory. They often operate on a variety of proprietary protocols and may not support the advanced security features of their larger counterparts. Moreover, the sheer number of devices and their diverse functionality pose a significant management challenge. A modern approach to securing IoT devices involves a multi-layered strategy that goes beyond simply deploying a firewall. This includes implementing strong authentication methods, regularly updating device firmware, and segmenting the network to isolate vulnerable devices. It's a complex picture but one that requires careful consideration and a proactive approach.
One of the primary challenges in securing IoT devices is the lack of standardized security protocols. Unlike computers and smartphones, which benefit from established security standards, IoT devices often operate in a fragmented ecosystem. Manufacturers prioritize functionality and cost-effectiveness over security, leading to devices that are vulnerable to a range of attacks. The default settings on many IoT devices are often weak or easily guessable, making them easy targets for hackers. Moreover, the software running on these devices is frequently outdated and lacks the necessary security patches to address known vulnerabilities. The situation is further complicated by the fact that many users are unaware of the security risks associated with IoT devices and are not adequately trained to protect them.
Firewall solutions for IoT devices can take various forms. Some are hardware-based, providing physical protection at the network perimeter. Others are software-based, running on the devices themselves or on a central gateway. The most effective solutions often combine both approaches. A hardware firewall at the network edge can provide a first line of defense, filtering malicious traffic before it reaches the internal network. Software-based firewalls on individual devices can provide more granular control, monitoring and filtering traffic based on specific device characteristics and behavior. The choice of firewall solution will depend on the specific requirements of the network and the types of IoT devices being used.
Consider the rise of botnets, networks of compromised devices controlled by attackers. IoT devices are a favorite target for botnet operators because of their ubiquity and weak security. Once infected, these devices can be used to launch distributed denial-of-service (DDoS) attacks, overwhelming websites and online services with traffic. They can also be used to spread malware and steal sensitive data. The Mirai botnet, which infected hundreds of thousands of IoT devices, is a prime example of the devastating impact that botnets can have. Effective firewall solutions, coupled with proactive threat intelligence, are crucial for mitigating the risk of botnet attacks.
Network segmentation is another important security measure. By dividing the network into smaller, isolated segments, you can limit the impact of a security breach. If one IoT device is compromised, the attacker's access is restricted to that segment, preventing them from spreading to other devices or accessing sensitive data. This also makes it easier to monitor and manage network traffic, and to identify and respond to security incidents. Firewalls play a key role in network segmentation, allowing you to define rules and policies for each segment, controlling the flow of traffic between them.
The evolving landscape of IoT security requires constant vigilance and adaptation. New threats emerge regularly, and existing vulnerabilities are constantly being exploited. Staying informed about the latest security threats and best practices is essential for protecting your IoT devices. This includes subscribing to security newsletters, reading industry publications, and attending security conferences. Moreover, it's important to regularly update the firmware and software on your devices, as these updates often include important security patches. If you don't regularly update the firmware, your devices will be more susceptible to being hacked. Also, be wary of downloading files or clicking links from unfamiliar sources.
The importance of user education cannot be overstated. Many security breaches are the result of human error. Users need to be educated about the security risks associated with IoT devices and how to protect themselves. This includes changing default passwords, enabling two-factor authentication, and being careful about the information they share online. They need to be trained to recognize phishing attempts and other social engineering tactics. Many users install devices without understanding the implications for security. It is a responsibility of the manufacturers to explain in detail what their device does and the risks associated with their use.
Beyond firewalls, there are other security measures that can be implemented to protect IoT devices. These include:
- Strong authentication: Using strong passwords and multi-factor authentication can help prevent unauthorized access to your devices.
- Regular firmware updates: Manufacturers often release firmware updates to fix security vulnerabilities, so it's important to keep your devices updated.
- Network monitoring: Monitoring your network traffic can help you identify suspicious activity and potential security threats.
- Data encryption: Encrypting data at rest and in transit can protect it from unauthorized access.
- Vulnerability scanning: Regularly scanning your devices for vulnerabilities can help you identify and fix potential security flaws.
The future of IoT security will likely involve a combination of technologies and approaches. Artificial intelligence (AI) and machine learning (ML) are being used to detect and respond to threats in real-time. Blockchain technology is being explored as a way to secure device identities and data. Security-by-design, which incorporates security considerations into the development process from the outset, is becoming increasingly important. The industry is moving toward a more proactive and holistic approach to IoT security, where security is not an afterthought but an integral part of the device lifecycle.
Choosing the right firewall for your IoT devices involves careful consideration of several factors. First, assess your network and identify the types of IoT devices you are using. Next, determine the level of security you need. Consider the potential risks and the sensitivity of the data being handled by your devices. Research the various firewall solutions available, comparing their features, performance, and price. Look for solutions that offer strong security features, such as deep packet inspection, intrusion detection and prevention, and traffic monitoring. Ensure that the solution is compatible with your IoT devices and is easy to manage. Be mindful of the long-term maintenance costs. Finally, test the firewall solution thoroughly before deploying it in your network.
In conclusion, securing IoT devices is a complex but essential task. The increasing number of connected devices and the sophistication of cyber threats require a proactive and multi-layered approach. While firewalls are a critical component of any IoT security strategy, they are not a silver bullet. They must be combined with other security measures, such as strong authentication, network segmentation, and regular firmware updates. Educating users about the risks associated with IoT devices and providing them with the knowledge and tools they need to protect themselves is also essential. By taking a comprehensive approach to IoT security, you can significantly reduce your risk and protect your data and privacy.
| Aspect | Details | Relevance to Firewall IoT Devices |
| Vulnerability Assessment | Identifying weaknesses in IoT devices, firmware, software, and network configurations. | Firewalls help protect against exploits that leverage known vulnerabilities by blocking malicious traffic. |
| Threat Modeling | Analyzing potential threats and attack vectors to assess risks and devise mitigation strategies. | Firewalls are configured based on threat models, defining traffic rules to prevent identified attacks. |
| Network Segmentation | Dividing a network into isolated segments to contain potential breaches and limit lateral movement. | Firewalls are instrumental in implementing network segmentation, controlling traffic between segments. |
| Intrusion Detection and Prevention Systems (IDPS) | Monitoring network traffic for malicious activity and automatically blocking or mitigating threats. | Advanced firewalls integrate IDPS capabilities to detect and block suspicious behavior. |
| Access Control | Restricting access to network resources based on identity, roles, and policies. | Firewalls enforce access control policies, permitting only authorized devices and users to access the network. |
| Data Encryption | Protecting data confidentiality by encoding information to make it unreadable without a decryption key. | Firewalls often support encrypted communication, and inspect traffic passing through secure tunnels. |
| Regular Firmware and Software Updates | Keeping devices up to date with the latest security patches and bug fixes. | Firewalls protect devices that cannot or have not been updated. |
| User Training and Awareness | Educating users about security risks and best practices to prevent social engineering and human error. | Firewalls are less effective without educated users. Good training reduces the chances of a user being tricked. |
| Incident Response | Procedures for detecting, containing, eradicating, and recovering from security incidents. | Firewalls assist in incident response by providing logs and alerts related to suspicious activities. |
| Remote Access Management | Securely managing remote access to IoT devices for maintenance, monitoring, and control. | Firewalls protect against unauthorized remote access attempts. |
| Monitoring and Logging | Continuous surveillance of network traffic and activity, with detailed records for analysis. | Firewalls generate logs that can be used for monitoring and incident response. |
| Compliance | Adhering to industry standards and regulations (e.g., HIPAA, GDPR) related to data security. | Firewalls are part of the measures used to ensure the compliance of the organization or individual. |
| AI and Machine Learning in Security | Using artificial intelligence and machine learning to detect advanced threats and automate security responses. | Firewalls incorporate AI/ML to adapt to sophisticated attacks and reduce human intervention. |
| Zero-Trust Security | A security model based on the principle "never trust, always verify". | Firewalls support the implementation of Zero-Trust by enforcing granular access control. |
| Supply Chain Security | Security measures throughout the device and software development and distribution process. | Firewalls are a defense in depth measure that adds security at the point of use of an IoT device. |
For further reading on general cybersecurity best practices, you can reference the following website: CISA Cybersecurity Best Practices