SSH For IoT: Secure Access & Control Guide
Is the future of your Internet of Things (IoT) infrastructure as secure and manageable as it needs to be? In an increasingly interconnected world, the ability to securely access and control your IoT devices from anywhere is no longer a luxury, but a necessity.
The proliferation of connected devices has created a complex landscape, one that demands robust security measures and efficient management tools. Traditional methods of device administration are rapidly becoming obsolete, leaving many organizations vulnerable. This article will illuminate how Secure Shell (SSH) protocol can revolutionize your approach to IoT device management, empowering you to maintain control, enhance security, and streamline operations. We will explore the core principles of SSH, delve into its practical applications within the IoT ecosystem, and provide a step-by-step guide to implementing SSH control on your devices. As the adoption of IoT solutions continues to accelerate, the importance of understanding and leveraging secure remote access becomes paramount. This comprehensive guide is designed to equip you with the knowledge and skills necessary to navigate the challenges and capitalize on the opportunities presented by this transformative technology.
| Category | Details |
|---|---|
| Technology Focus | Secure Shell (SSH) Protocol for IoT Device Management |
| Core Functionality | Secure Remote Access, Device Configuration, File Transfer, System Monitoring |
| Key Benefits | Enhanced Security, Reduced Downtime, Improved Efficiency, Scalability, Standardization |
| Target Audience | IoT Device Administrators, Network Engineers, Security Professionals, Businesses utilizing IoT solutions |
| Related Technologies | Raspberry Pi, AWS, Windows 10, Operating Systems (Linux, Unix) |
| Industry Impact | Provides a standardized approach to device management, allowing administrators to execute commands, transfer files, and monitor system performance securely. |
| Reference Website | SSH.com |
Overall, SSH is a vital tool for secure remote administration and management, enabling users to securely access and control their IoT devices. Its encryption and authentication capabilities make SSH an essential component in ensuring the privacy and security of IoT deployments. The primary function of SSH in an IoT environment is to establish a secure channel for remote access, allowing administrators to manage and troubleshoot devices from a distance. This includes tasks such as updating software, configuring settings, monitoring system performance, and transferring files. The ability to perform these operations remotely is a significant advantage, reducing the need for physical presence and enabling efficient management of large-scale deployments.
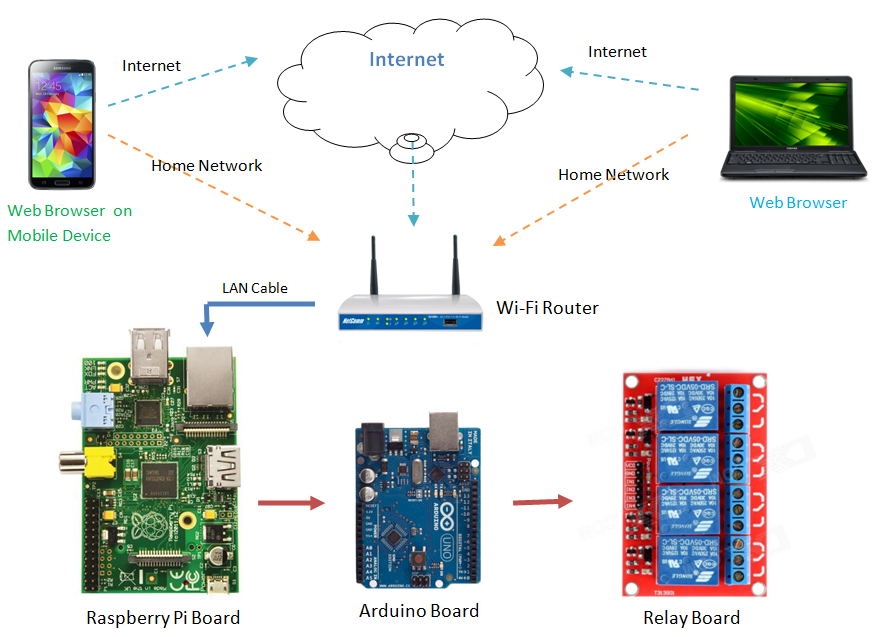
To establish a remote SSH connection, several steps are necessary. The initial requirement is to obtain the IP address of the IoT device. This address can often be found either on the device itself or through the network router that it is connected to. Following this, the IoT device needs to be configured to accept SSH connections. This generally involves ensuring that an SSH server is installed and running on the device. The specific steps for installation and configuration will vary depending on the operating system of the device, but the underlying principle remains the same: to create a secure listening point for remote connections. Once the device is configured, proper network settings, including firewall rules, must be verified to allow SSH traffic to pass through. This ensures that the connection can be established successfully from a remote location.
The benefits of using SSH for IoT devices are numerous and compelling. Remote SSH access lets you stay in control, reduce downtime, and improve your IoT device management by eliminating the need to be physically near your device. One of the most significant advantages is the enhanced security it provides. SSH employs strong encryption to protect data in transit, safeguarding sensitive information from interception and unauthorized access. Furthermore, SSH supports robust authentication mechanisms, such as public-key authentication, which adds an extra layer of security. This is critical in preventing unauthorized users from gaining control of the devices. Another major benefit is the efficiency it brings to device management. Administrators can execute commands, transfer files, and monitor system performance securely without having to travel to the location of the devices. This is especially valuable in environments where devices are deployed across vast geographical areas or in hard-to-reach locations.
As more businesses adopt IoT solutions, secure remote access to devices through SSH becomes critical. Moreover, SSH offers a standardized approach to device management, allowing administrators to execute commands, transfer files, and monitor system performance securely. The protocol's versatility and widespread adoption make it a highly adaptable solution. The scalability of SSH is also noteworthy. It can easily accommodate a growing number of IoT devices, making it an ideal solution for organizations that are expanding their IoT deployments. SSH works seamlessly with a wide range of devices and operating systems, including Linux, Unix-based systems, and Windows 10, providing a versatile solution for IoT. This interoperability ensures that it can be used across diverse hardware and software environments.
Setting up SSH for IoT devices involves several practical steps. First, you need to install an SSH server on the IoT device. The installation process varies depending on the operating system of the device. For example, on a Raspberry Pi, enabling SSH is relatively simple. The most common approach is to use a package manager, such as apt, to install an SSH server like OpenSSH. After installation, the SSH server needs to be configured. This often involves setting up user accounts, configuring authentication methods, and adjusting security settings. It's crucial to ensure that strong passwords or, preferably, key-based authentication are used. Once the server is configured, you can test the connection by attempting to SSH into the device from another machine. This will help to verify that the setup has been completed correctly.
Enabling SSH on your IoT device is a straightforward process, but the exact steps may vary depending on the device and the operating system it runs on. Below are general guidelines for enabling SSH on common IoT platforms.
Enabling SSH on a Raspberry Pi:
Raspberry Pi is one of the most popular IoT platforms, and enabling SSH is relatively simple. The process typically involves the following steps:
- Update the system: Ensure that your Raspberry Pi's software is up-to-date by running the command:
sudo apt update && sudo apt upgrade. - Enable SSH through configuration: Use the Raspberry Pi configuration tool (
sudo raspi-config). - Enable the SSH service: Select the 'Interface Options' and then 'SSH' to enable the service.
- Set a strong password: For the default 'pi' user, it's important to change the default password by running the command
passwd pi - Check IP Address: Find the IP address of your Raspberry Pi. This can be done through the command
ifconfigor by checking your router's connected devices. - Connect using SSH: From a terminal on your computer, use the command
ssh pi@, replacing
This provides a basic framework for enabling SSH on the Raspberry Pi, a common starting point for many IoT projects.
Consider the challenges that arise with traditional management methods when you have millions of connected devices worldwide. Traditional management methods have become inadequate. Consider the limitations of manual configuration, physical access requirements, and the security risks associated with outdated practices. SSH control offers a standardized approach to device management, allowing administrators to execute commands, transfer files, and monitor system performance securely. The protocol's efficiency, security, and scalability make it a must-have for modern IoT deployments.
To "take control of your IoT devices with SSH on Windows 10" provides a specific application of SSH. For Windows 10 users, the process usually involves enabling the SSH client or using a third-party SSH client like PuTTY or MobaXterm. After installing an SSH client, you will need to know the IP address of the IoT device to establish a connection. You can then use the client to connect to the device. The specific steps may vary depending on your chosen SSH client, but the basic workflow remains consistent. Start by entering the IP address of the IoT device, specifying the username and password (or using key-based authentication), and initiating the connection. Once connected, you can execute commands and manage your device remotely.
This article provides a comprehensive guide to using SSH IoT from anywhere on Windows 10. By following the steps outlined in this article, you can securely and conveniently manage your IoT devices no matter where you are. Remember to prioritize security and explore advanced configuration options to tailor SSH to your specific requirements and environment. This involves choosing strong passwords, using key-based authentication, and regularly updating your devices software and SSH server. Additional measures include configuring firewalls and implementing network segmentation to isolate your IoT devices from your other systems. This protocol has become the industry standard for IoT device management due to its versatility and security features.
Establishing a remote SSH connection involves several steps, including configuring the IoT device, setting up the SSH server, and ensuring proper network settings. First, the IoT device must be prepared for SSH access. This preparation involves installing and configuring an SSH server. The specific steps depend on the operating system of the IoT device, but generally, you'll need to install an SSH server package and configure it for your network. Second, you'll need to ensure that your network settings are configured to allow SSH traffic. This might include configuring your router to forward SSH traffic to the correct internal IP address of your IoT device. Finally, you need to use an SSH client on your computer to connect to the IoT device. This client will allow you to securely access the device's command-line interface.
As more businesses adopt IoT solutions, secure remote access to devices through SSH becomes critical. This is especially true for businesses that deploy IoT devices in remote locations or require constant monitoring and maintenance. SSH provides a secure and efficient way to manage these devices, reducing downtime and improving overall operational efficiency. This article has delved into the essential aspects of IoT SSH control, providing you with actionable insights and best practices. The information provided here can serve as a foundation for creating a robust and secure IoT infrastructure.