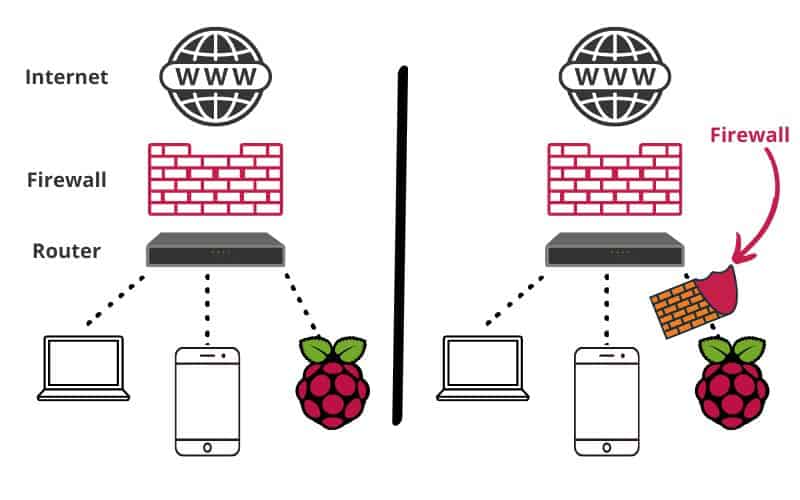
Secure Your Home: Network Firewall On Raspberry Pi Guide
Is your home or small business network truly secure in the digital age? The integration of a network firewall using a Raspberry Pi offers a powerful, cost-effective solution for enhanced cybersecurity, safeguarding your digital life from a multitude of threats.
The modern internet landscape is a minefield of potential dangers. From malware and ransomware to phishing scams and data breaches, the threats are constant and evolving. Traditional routers often provide a basic level of firewall protection, but they frequently lack the granular control and sophisticated features needed to effectively repel modern cyberattacks. This is where the Raspberry Pi, a small, affordable, and versatile single-board computer, shines. Coupled with the right software, it can be transformed into a highly capable network firewall, offering a robust defense against a wide range of online threats. The beauty of this approach lies not only in its enhanced security but also in its affordability and customizability, making it an attractive option for individuals, families, and small businesses alike. Building a firewall with a Raspberry Pi empowers users to take control of their network security, moving beyond the limitations of pre-configured solutions and tailoring their defenses to their specific needs. The process, while requiring some technical knowledge, is well-documented and readily achievable with readily available resources. It's a proactive step towards creating a safer online environment. The appeal of a Raspberry Pi firewall extends beyond simple protection; it also provides opportunities for learning, experimentation, and a deeper understanding of how networks function. It is an investment in digital self-reliance.
The core function of a network firewall, whether hardware or software-based, is to control network traffic. It acts as a gatekeeper, examining incoming and outgoing data packets and determining whether they should be allowed to pass through. This is achieved through a set of rules that define what is permitted and what is blocked. In the context of a Raspberry Pi firewall, this functionality is typically provided by software like `iptables` (the standard Linux firewall), `nftables` (its more modern replacement), or specialized firewall distributions. These tools allow users to create highly specific rules, filtering traffic based on source and destination IP addresses, ports, protocols, and other criteria. The granularity of control is what makes a Raspberry Pi firewall so effective, allowing administrators to block specific types of traffic, prevent access to malicious websites, and even implement intrusion detection and prevention systems. Properly configured, a Raspberry Pi firewall provides a first line of defense, significantly reducing the attack surface of the network. This proactive approach to network security is far superior to relying solely on reactive measures, such as antivirus software, which may only detect threats after they have already infiltrated the system.
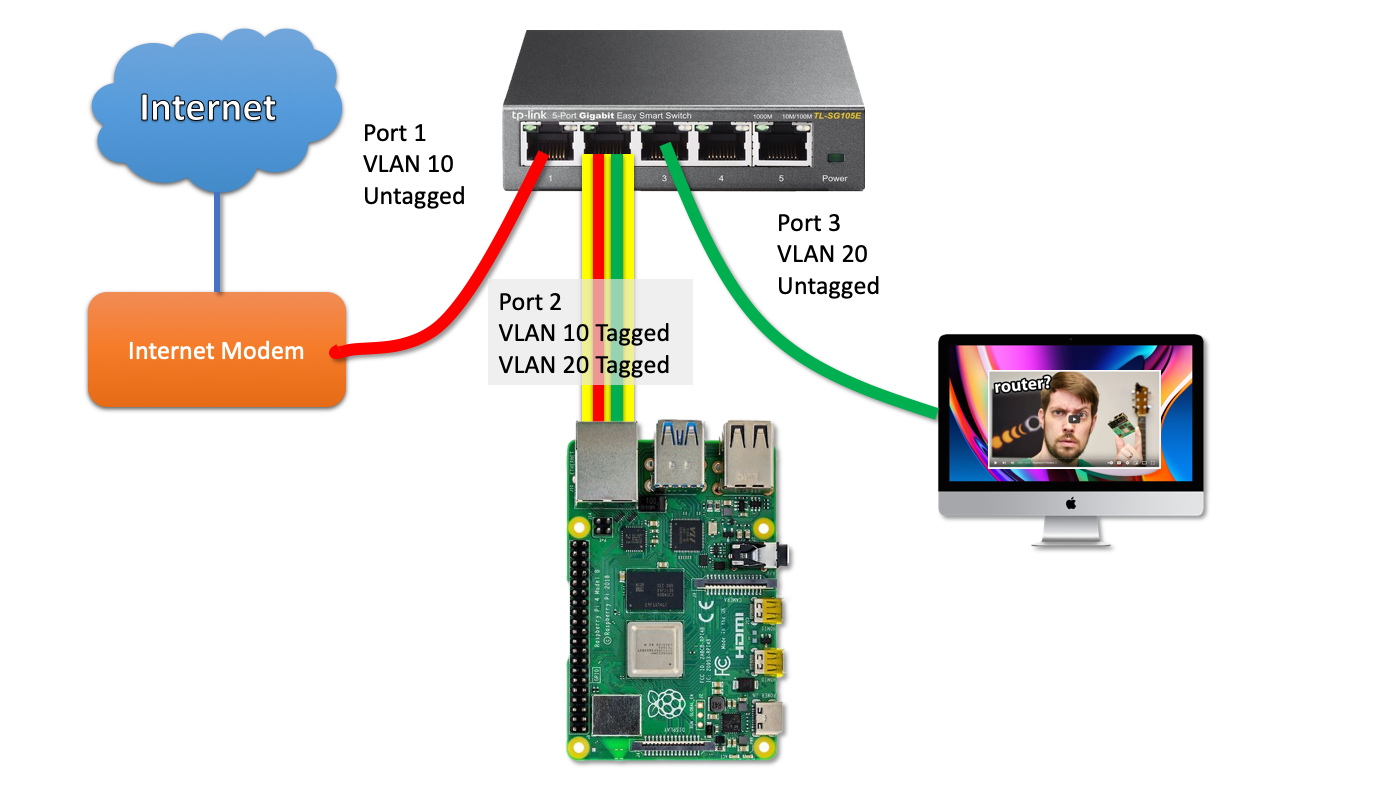
Choosing the right Raspberry Pi model is the first step. The Raspberry Pi 4 Model B is generally recommended for its performance capabilities, including its Gigabit Ethernet port and processing power. However, older models like the Raspberry Pi 3 Model B+ can also be used, although they may offer slightly less performance, especially under heavy network load. The choice of model depends on the specific needs of the network and the level of security required. Once the hardware is selected, the next consideration is the operating system. While a general-purpose Linux distribution like Debian or Ubuntu can be used, specialized firewall distributions are often preferred. These distributions, such as pfSense or IPFire, come pre-configured with firewall software and a user-friendly web interface, simplifying the setup and management process. They also provide advanced features like VPN support, intrusion detection, and traffic shaping, making them ideal for those who want a more comprehensive security solution. Regardless of the operating system chosen, the basic setup involves installing the operating system on an SD card, connecting the Raspberry Pi to the network, and configuring the firewall rules. This process typically involves accessing the firewall's web interface or using the command-line interface to define the rules that will govern network traffic.
Installing and configuring a network firewall on a Raspberry Pi requires a basic understanding of networking concepts, such as IP addresses, ports, and protocols. Familiarity with the command line interface is also beneficial, although the web interfaces provided by some firewall distributions can significantly simplify the configuration process. The core of the firewall's functionality revolves around the creation of rules that define which traffic is permitted and which is blocked. These rules are organized into chains, which specify the order in which the traffic is processed. Common chains include INPUT, OUTPUT, and FORWARD. The INPUT chain governs traffic destined for the Raspberry Pi itself, the OUTPUT chain governs traffic originating from the Raspberry Pi, and the FORWARD chain governs traffic that is being routed through the Raspberry Pi. When creating firewall rules, it is important to adopt a "deny-all-by-default" approach. This means that by default, all traffic is blocked, and only specific traffic that is explicitly allowed is permitted to pass through. This approach minimizes the attack surface by preventing all unauthorized access. The rules are then configured to allow only the necessary traffic, such as connections to the internet, access to internal network resources, and any other services that need to be accessible. The rules can be based on various criteria, including source and destination IP addresses, ports, protocols, and even the content of the packets. The more granular the rules, the more secure the firewall becomes.
One of the key advantages of a Raspberry Pi firewall is its ability to provide network address translation (NAT). NAT allows multiple devices on a private network to share a single public IP address, effectively hiding the internal network from the internet. This is a crucial security feature, as it prevents direct access to devices on the internal network, reducing the risk of attack. The Raspberry Pi, acting as the NAT router, translates the private IP addresses of the internal devices to its public IP address when they communicate with the internet. This process also involves port forwarding, which allows specific services on the internal network to be accessed from the internet. For example, if a user is running a web server on a device on their internal network, they can configure the firewall to forward traffic on port 80 (the standard HTTP port) to that device. NAT is a fundamental component of modern home and small business networks, and the Raspberry Pi provides an efficient and cost-effective way to implement it.
Beyond the basic firewall functionality, Raspberry Pi firewalls can be extended with additional security features. One popular option is the implementation of a virtual private network (VPN). A VPN encrypts all network traffic, providing a secure and private connection over the internet. This is particularly useful for accessing public Wi-Fi networks, where the risk of eavesdropping and data theft is high. The Raspberry Pi can be configured as a VPN server, allowing users to securely connect to their home network from anywhere in the world. This provides a secure tunnel for browsing the internet, accessing files, and using other network resources. Various VPN protocols can be implemented, including OpenVPN and WireGuard, with each offering its own advantages in terms of security, performance, and ease of configuration. Another common feature is intrusion detection and prevention (IDS/IPS). IDS/IPS systems monitor network traffic for malicious activity, such as port scans, malware infections, and unauthorized access attempts. If suspicious activity is detected, the IDS/IPS system can generate alerts, log the events, and even block the offending traffic. Tools like Snort and Suricata can be used to implement IDS/IPS functionality on a Raspberry Pi. These tools analyze network traffic against a database of known threats and can identify and block malicious activity in real-time.
Regular maintenance and updates are essential for maintaining the security of a Raspberry Pi firewall. This includes keeping the operating system, firewall software, and any installed applications up to date. Security updates often address vulnerabilities and bugs that can be exploited by attackers, so it is important to apply them promptly. The update process typically involves using the package manager of the operating system to download and install the latest updates. It is also important to regularly review the firewall rules and logs. The firewall logs provide valuable information about network activity, including any blocked connections and potential security threats. Reviewing these logs can help identify suspicious activity and allow users to fine-tune their firewall rules to improve security. In addition to software updates, the physical security of the Raspberry Pi should also be considered. The device should be placed in a secure location, protected from unauthorized access or tampering. If the Raspberry Pi is running sensitive services, such as a VPN server, it is also advisable to implement additional security measures, such as multi-factor authentication. By following these maintenance practices, users can ensure that their Raspberry Pi firewall remains a robust and effective defense against cyber threats.
The benefits of using a Raspberry Pi as a network firewall are substantial. Firstly, the cost-effectiveness is undeniable. Compared to commercial firewall appliances, a Raspberry Pi firewall is significantly cheaper, requiring only the cost of the Raspberry Pi itself, an SD card, and potentially an Ethernet cable. Secondly, the level of customization is unparalleled. Users have complete control over the firewall configuration and can tailor it to their specific needs. Thirdly, the enhanced security provides a significant advantage over traditional router-based firewalls. The Raspberry Pi firewall offers more granular control, enabling users to block specific types of traffic and implement advanced security features. Furthermore, it offers educational value. Building and maintaining a Raspberry Pi firewall is a great way to learn about networking and cybersecurity. By understanding how the firewall works, users can gain a deeper appreciation for the threats they face and how to protect themselves. In the long run, this knowledge can be invaluable in navigating the increasingly complex digital world. The Raspberry Pi firewall empowers users to take control of their network security, fostering a proactive and informed approach to protecting their digital assets.
The transition to a Raspberry Pi firewall can seem daunting at first, but it is a manageable process, particularly for those with some technical aptitude. The initial setup requires a basic understanding of networking concepts, such as IP addresses, ports, and protocols. However, there are numerous online resources, tutorials, and communities that can guide users through the process. The Raspberry Pi Foundation website provides extensive documentation and resources. Various websites and forums offer step-by-step guides and troubleshooting assistance. Moreover, there are pre-configured firewall distributions available, such as pfSense and IPFire, that simplify the setup process. These distributions provide a user-friendly web interface, making it easier to configure and manage the firewall. The key is to start with a clear understanding of the network environment and the security goals. This will help in defining the firewall rules and configuring the network settings. It is also recommended to test the firewall thoroughly after setup to ensure that it is functioning as expected. By taking a systematic approach and utilizing the available resources, anyone can build and maintain a secure and effective network firewall using a Raspberry Pi. The effort is well worth it, offering a powerful defense against the constant and evolving threats of the internet.
Consider the practical applications of a Raspberry Pi firewall in various scenarios. For home users, the firewall can protect against malware, phishing scams, and unauthorized access. It can also be used to control network access for children, blocking access to inappropriate websites or limiting internet usage during specific times. For small businesses, a Raspberry Pi firewall can provide a first line of defense against cyberattacks, protecting sensitive data and preventing costly downtime. It can also be used to secure remote access to the network, allowing employees to work from home securely. For those interested in privacy, a Raspberry Pi firewall can be combined with a VPN to encrypt all network traffic, preventing eavesdropping and ensuring online anonymity. The possibilities are endless. The Raspberry Pi firewall is a versatile tool that can be adapted to meet a wide range of security needs. From protecting a home network to securing a small business, it offers a cost-effective and customizable solution that empowers users to take control of their digital security. The ease of use and wealth of available resources make it a readily accessible option for anyone seeking to enhance their online security.
Looking towards the future, the role of network firewalls, and specifically those implemented on platforms like the Raspberry Pi, will likely continue to evolve. As the internet becomes increasingly complex and the threat landscape grows, the need for robust and adaptable security solutions will become even greater. Raspberry Pi firewalls are well-positioned to meet this challenge. Their affordability and customizability make them ideal for adapting to new threats and incorporating new security features. The open-source nature of the software allows for community development and innovation. Developers and security researchers are constantly working to improve the performance, security, and ease of use of these systems. We can expect to see advancements in areas such as intrusion detection and prevention, traffic analysis, and VPN technology. Integration with the Internet of Things (IoT) is another area of potential growth. As more and more devices connect to the internet, the need to secure them becomes increasingly important. Raspberry Pi firewalls can be used to protect IoT devices from malware and unauthorized access, creating a more secure and reliable smart home or office environment. The continued evolution of the Raspberry Pi platform, with its increased processing power and networking capabilities, will further enhance its suitability for this role. In conclusion, the future of network firewalls, especially those built on the Raspberry Pi platform, is bright. They offer a cost-effective, customizable, and adaptable solution for securing networks of all sizes, and their importance will only continue to grow in the years to come. The proactive approach to cybersecurity they embody is a testament to the power of user empowerment and a commitment to digital safety.
In summary, the "network firewall raspberry pi" solution represents a powerful and accessible approach to bolstering network security. By leveraging the capabilities of a small, affordable, and customizable Raspberry Pi, users can establish a robust defense against a wide range of cyber threats. The article has covered the essential aspects of this solution, from the basic principles of firewalls and choosing the right hardware to the installation, configuration, and ongoing maintenance. It has also emphasized the benefits, which include enhanced security, cost-effectiveness, customizability, and the opportunity to learn more about networking and cybersecurity. This proactive approach to cybersecurity is not only effective but also empowers users to control their digital environment, mitigating the risks of the ever-evolving threat landscape. The resources provided in this article offer practical guidance, while the concluding thoughts highlight the increasing importance of these solutions in the future. The integration of a network firewall using a Raspberry Pi is a smart and proactive step towards a safer digital life, for individuals, families, and small businesses alike.