Secure Your Pi: SSH Port Guide & Best Practices
Is securing your server's SSH port a battle you're constantly fighting? The seemingly innocuous SSH port, often set to the standard port 22, is a prime target for malicious actors, making its protection an absolute necessity in the digital age.
Understanding the vulnerability is the first step toward fortifying your defenses. The SSH (Secure Shell) protocol, a cornerstone of remote server administration and secure data transfer, relies on this port for communication. Its default setting, however, is a well-known secret, making it an easy target for automated bots and determined hackers constantly scanning the internet for open connections. Once access is gained, attackers can attempt brute-force attacks, credential stuffing, or even launch sophisticated attacks that can compromise your entire system. Consequently, the security of your SSH port is far more critical than many realize, demanding constant vigilance and proactive measures.
To delve further into the intricacies of protecting your SSH port, let's examine the essential strategies and best practices that will help bolster your server's security posture.
One of the most fundamental steps in securing your SSH port is changing the default port number. This seemingly simple action can significantly deter automated bots and script kiddies who are actively scanning for the standard port 22. By selecting a non-standard, high-numbered port (e.g., 22222 or higher) you immediately reduce the attack surface. The key here is obscurity, not security in itself, but it buys you valuable time and reduces the number of automated probes your server receives. Changing the port is usually a straightforward configuration task. You'll typically modify the `sshd_config` file, a configuration file typically located in `/etc/ssh/`, and then restart the SSH service. This is a must-do step, almost universally recommended.
Beyond changing the port, enforcing strong password policies and employing multi-factor authentication (MFA) are critical. Strong passwords, consisting of a combination of uppercase and lowercase letters, numbers, and symbols, are the first line of defense against brute-force attacks. Passwords should be complex, unique, and regularly changed. Multi-factor authentication, adding another layer of security, goes beyond the password. It typically involves a second authentication factor, such as a one-time code generated by an authenticator app (Google Authenticator or Authy) or a hardware security key. If an attacker manages to get your password, they will still need the second factor to gain access, thus significantly mitigating the risk.
Furthermore, implementing SSH key-based authentication is considered highly secure and significantly reduces the risk associated with password-based authentication. This involves generating a cryptographic key pair: a private key that resides on the client machine and a public key that is placed on the server. When a user attempts to connect, the server challenges the client to prove possession of the corresponding private key. This is a significantly more secure method than passwords, as it's resistant to brute-force and dictionary attacks. This key-based authentication is often combined with disabling password authentication altogether for an even more robust security posture.
Rate limiting and intrusion detection systems (IDS) play a crucial role in proactively monitoring and responding to potential attacks. Rate limiting restricts the number of failed login attempts from a single IP address within a specified time frame. This prevents attackers from repeatedly trying different passwords in a brute-force attack. An IDS, on the other hand, analyzes network traffic and system logs for suspicious activity. If an IDS detects a series of failed login attempts, it can automatically block the offending IP address, preventing further attacks. Implementing both rate limiting and an IDS significantly enhances your ability to detect and respond to malicious activities in real-time.
Regularly updating and patching your server's operating system and SSH software is crucial. Security vulnerabilities are frequently discovered and fixed in software updates. If you fail to apply these patches, you leave yourself open to attacks. By keeping your system updated, you ensure you have the latest security fixes and are less vulnerable to known exploits. Setting up automated updates or subscribing to security alerts is a good practice to stay informed about critical patches and vulnerabilities.
Disabling root login via SSH is another fundamental security measure. Root access grants complete control over the server, and if compromised, can lead to catastrophic consequences. Disabling root login and creating a separate user account with sudo privileges significantly reduces the attack surface. This practice forces attackers to first compromise a less privileged user account before they can attempt to escalate privileges. Its a simple but effective way to protect your server.
Firewall configuration is your first line of defense and is crucial for controlling network traffic. Firewalls, whether hardware or software-based, allow you to control the traffic entering and leaving your server. You can configure your firewall to only allow SSH traffic from specific IP addresses or IP ranges, effectively limiting access to authorized users. This greatly reduces the risk of unauthorized access. Ensure that the firewall is properly configured and that only necessary ports are open. Tools like `iptables` (on Linux) or the built-in firewall on Windows Server can be used for this purpose. Regularly review firewall rules to ensure they are up-to-date and accurately reflect your security requirements.
Beyond the technical measures, understanding the logs is crucial. Regular monitoring of SSH logs is essential for detecting suspicious activity. SSH logs contain valuable information about login attempts, successful logins, and failed attempts. Analyzing these logs helps you identify potential attacks or unusual behavior. Look for patterns like multiple failed login attempts from the same IP address, logins from unusual locations, or logins outside of your normal hours. Tools such as `fail2ban` can automate the process of monitoring logs and banning suspicious IPs. By actively monitoring your SSH logs, you gain valuable insights into your server's security posture and can proactively respond to threats.
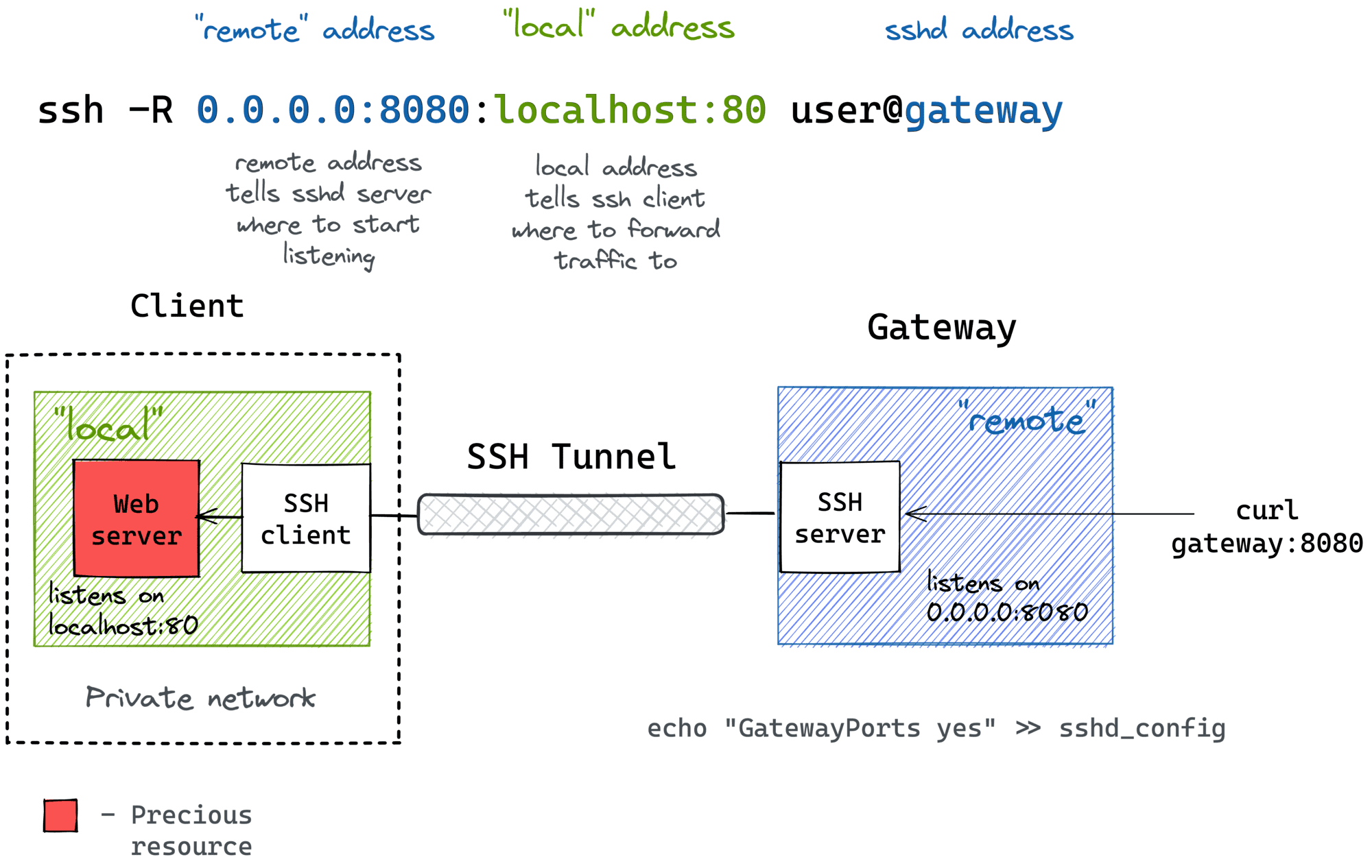
Consider implementing SSH tunneling or port forwarding, especially if you need to access internal network resources securely. SSH tunneling encrypts the communication between your client machine and the server, providing a secure channel for accessing services. This can be used to bypass firewall restrictions or encrypt traffic for web browsing or other services. SSH port forwarding can be used to forward traffic from a local port on your client machine to a remote port on the server, enabling secure access to services within your network. Properly configured, these techniques enhance security and offer flexibility in accessing network resources.
When setting up your SSH configuration, pay close attention to options like `MaxAuthTries` and `LoginGraceTime`. The `MaxAuthTries` option specifies the number of attempts a user has to authenticate before the connection is closed. Reducing this value can mitigate the impact of brute-force attacks. The `LoginGraceTime` option determines the amount of time a user has to successfully authenticate. Setting a reasonable time frame will limit the window of opportunity for attackers. These parameters, along with other SSH configuration options, provide a high level of granular control over the security of your SSH service. Regularly review and tune these settings to align with your specific security needs.
The principle of least privilege dictates that users should be granted only the minimum level of access required to perform their tasks. This principle applies to SSH access as well. Avoid granting unnecessary privileges to user accounts that connect via SSH. Limit the commands users can execute or restrict their access to specific directories. This principle, when implemented consistently, can limit the damage an attacker can do if they manage to compromise a user account. Implement role-based access control (RBAC) to manage user permissions more effectively and simplify the task of ensuring that each user has only the necessary level of access.
Security audits, conducted periodically, will help to identify vulnerabilities. Regularly review your SSH configuration and security measures to ensure they are still effective. This could involve penetration testing or vulnerability scans, or simply a review of your SSH logs, configuration files, and firewall rules. Addressing the weaknesses you find will help to strengthen the overall security of your system. Consider using automated tools or a security professional to perform these audits. This proactive approach will help you stay ahead of potential threats.
Documentation is also an indispensable part of secure server management. Thoroughly document your SSH configuration, including the port number, key-based authentication settings, firewall rules, and any other security measures you've implemented. Keep your documentation up-to-date and accessible to authorized personnel. This documentation is not only helpful for troubleshooting, but also provides a clear understanding of your security posture and aids in auditing. Clear documentation will make it easier to manage, secure, and maintain your SSH setup over time.
The security landscape is always changing, and so too must be your approach. You should continuously monitor and evaluate your security measures, seeking out and adopting new technologies and techniques as needed. Staying informed about the latest security threats and vulnerabilities allows you to make adjustments and maintain the security of your server. Subscribe to security newsletters, follow industry blogs and security experts, and attend relevant conferences and workshops. The only constant in security is change.
Finally, understand that no security measure is foolproof, and be prepared for a potential breach. Maintain regular backups of your server data. Implement an incident response plan to quickly contain and recover from a security incident. This plan should include steps to identify the source of the attack, isolate affected systems, notify relevant parties, and restore from backups. Having a robust incident response plan will help minimize the impact of a security breach and allow you to recover quickly.