Secure SSH Over Internet: Your Guide For 2024
Can you truly secure your digital life, even when navigating the vast, often treacherous, expanse of the internet? The answer, surprisingly, lies in a powerful yet often overlooked tool: SSH over the internet. This method offers a robust and encrypted pathway to access your servers and devices, effectively creating a secure tunnel through the chaotic digital landscape. It's a vital technique for anyone who values privacy and data integrity in todays connected world.
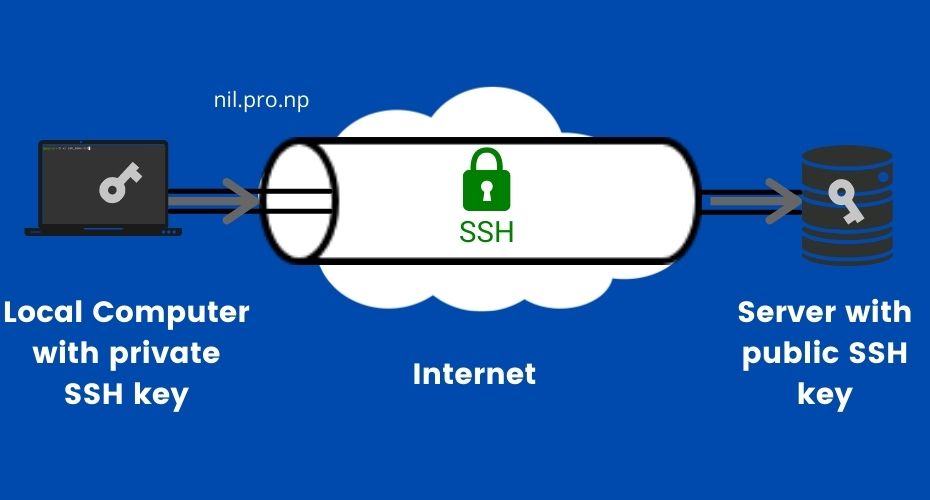
The fundamental principle is elegantly simple. Secure Shell (SSH) is a cryptographic network protocol used for secure data communication, remote command-line login, remote command execution, and other secure network services between two networked computers. When "SSH over the internet" is employed, this inherent security is extended, allowing you to connect to your home server, cloud instance, or any other device from anywhere in the world, as long as you have an internet connection. It's the digital equivalent of a heavily guarded, well-lit tunnel through a dark and dangerous forest. This ensures that all traffic is encrypted, protecting it from eavesdropping and tampering.
The effectiveness of SSH over the internet stems from its core design. SSH uses a combination of encryption techniques, including symmetric encryption (like AES), asymmetric encryption (like RSA or ECDSA), and hashing algorithms, to ensure confidentiality, integrity, and authentication. This makes it incredibly difficult for unauthorized parties to intercept and decipher your data. Furthermore, SSH supports key-based authentication, which is significantly more secure than traditional password-based authentication. With key-based authentication, you generate a pair of cryptographic keysa private key, which you keep secret, and a public key, which you can place on the server you want to access. When you attempt to connect, the server uses your public key to verify your identity, without you ever having to transmit your password over the network. This drastically reduces the risk of password compromise.
The implementation of SSH over the internet involves several key steps. First, you'll need an SSH server running on the target machine. This server listens for incoming connections on a specific port, typically port 22, although this can be customized for enhanced security. Next, you'll need an SSH client on the machine you are using to connect to the server. Most operating systems, including Linux, macOS, and Windows (through tools like PuTTY or the built-in OpenSSH client), have SSH clients pre-installed or readily available. The connection process involves specifying the hostname or IP address of the target server, the username, and the authentication method (password or key-based). Once connected, you can securely interact with the server, execute commands, transfer files, and more, all while the data is encrypted and protected. The security benefits are clear: you gain a secure channel for managing servers remotely, accessing files, and running applications, no matter your physical location. This capability is particularly useful for system administrators, developers, and anyone who needs secure access to their digital resources from anywhere with an internet connection. The practical application extends to setting up VPNs, securely tunneling web traffic, and securely transferring files using the `scp` command. The flexibility and control this provides are unparalleled.
However, using SSH over the internet isn't simply a matter of flipping a switch. There are several security considerations that must be addressed to ensure the integrity of your setup. The default configuration of an SSH server can be vulnerable to attacks if not properly secured. One of the first steps is to change the default port (22) to a non-standard port. This is a simple but effective way to reduce the number of automated attacks targeting your server. Another crucial step is to disable password-based authentication and enforce key-based authentication. This eliminates the possibility of brute-force attacks against weak passwords. Furthermore, you should regularly update your SSH server software to patch any security vulnerabilities. Consider implementing additional security measures, such as fail2ban, which automatically bans IP addresses that repeatedly fail to authenticate, further reducing the risk of unauthorized access. Proper configuration and regular monitoring are the cornerstones of a secure SSH implementation.
Beyond basic access, SSH over the internet can be leveraged for a myriad of advanced applications. One of the most popular uses is creating secure tunnels. An SSH tunnel effectively redirects network traffic through an encrypted SSH connection, allowing you to bypass firewalls, access geo-restricted content, or securely browse the internet. There are several types of SSH tunnels, including local port forwarding, remote port forwarding, and dynamic port forwarding (SOCKS proxy). Local port forwarding allows you to forward a port on your local machine to a port on the remote server, enabling you to access services running on the remote server as if they were running locally. Remote port forwarding does the opposite, forwarding a port on the remote server to a port on your local machine. Dynamic port forwarding, powered by a SOCKS proxy, allows you to forward all your internet traffic through the SSH connection, effectively creating a secure and private browsing experience. The versatility of SSH tunnels makes them a powerful tool for anyone who values privacy and security online.
Setting up an SSH tunnel is relatively straightforward. The basic syntax involves using the `-L`, `-R`, or `-D` flags with the `ssh` command to specify local, remote, or dynamic port forwarding, respectively. For local port forwarding, the command would look something like: `ssh -L 8080:localhost:80 user@remote_server`, which forwards port 8080 on your local machine to port 80 on the remote server. For remote port forwarding: `ssh -R 8080:localhost:80 user@remote_server`, which forwards port 8080 on the remote server to port 80 on your local machine. For dynamic port forwarding, the command is `ssh -D 1080 user@remote_server`, which establishes a SOCKS proxy on port 1080. Once the tunnel is established, you can configure your browser or other applications to use the specified port as a proxy, encrypting all traffic passing through it. Experimenting with these different types of tunnels offers flexibility and control over how you interact with the internet.
Another key advantage of SSH is its ability to securely transfer files. The `scp` (secure copy) command is a powerful utility built on top of the SSH protocol. It allows you to copy files between your local machine and a remote server securely. Unlike older file transfer protocols like FTP, `scp` encrypts all data transmitted between the client and the server, protecting your files from eavesdropping and tampering. The `scp` command uses a similar syntax to the `cp` command, but it requires you to specify the remote server's address and the username. For example, `scp local_file user@remote_server:/path/to/destination` copies `local_file` to the `/path/to/destination` directory on the remote server. This is a particularly useful tool for transferring sensitive documents, backups, or software updates. Beyond `scp`, `sftp` (secure FTP), another protocol built on SSH, offers more advanced file management capabilities, including directory browsing and resuming interrupted transfers. Both `scp` and `sftp` are essential tools for any system administrator or user who needs to manage files securely over the internet.
The security benefits extend beyond the protection of data in transit. SSH can also be used to harden the security of the remote system itself. By disabling unnecessary services and applying security patches regularly, the attack surface of the remote server is reduced. SSH provides a secure and efficient way to remotely administer these systems. For example, security patches can be applied and services can be restarted without physically being present at the server location. This remote administration capability is critical for maintaining the security and uptime of servers, and it is made significantly easier with the secure access afforded by SSH. By utilizing SSH, administrators can take proactive measures to prevent security breaches, and they can respond quickly to any potential vulnerabilities that are identified.
The deployment of SSH over the internet isn't without its challenges. One potential hurdle is dealing with firewalls and network address translation (NAT). Firewalls may block SSH traffic on port 22 (or your custom port), preventing you from connecting to your server. NAT, commonly used in home routers, translates private IP addresses to a public IP address, which can complicate the process of connecting to a server behind NAT. To overcome these challenges, you may need to configure port forwarding on your router to direct traffic from the public IP address to the internal IP address of your server. You may also need to explicitly allow SSH traffic through your firewall. However, once these configurations are done, accessing your resources becomes significantly more convenient and secure. Additionally, dynamic DNS services can be used to map a hostname to your dynamically changing IP address, further simplifying the connection process.
Another consideration is the potential performance impact. While SSH encryption is relatively lightweight, it can still introduce some overhead, especially when transferring large files or running computationally intensive commands. The performance impact will vary depending on the hardware, the network connection, and the chosen encryption algorithms. For high-bandwidth applications, it might be beneficial to choose a faster encryption algorithm, such as ChaCha20, that offers a good balance of speed and security. The overall performance impact is usually minimal for most everyday use cases, but it's worth keeping in mind if you plan on doing very heavy lifting over the SSH connection. Optimizing the SSH configuration, such as enabling compression, can also help to improve performance.
Finally, it's crucial to understand that while SSH over the internet provides a very strong level of security, it's not a silver bullet. It's only as secure as the weakest link in your system. This means that it's vital to secure your client machines, as well. Malware on your local machine could potentially compromise your SSH credentials, allowing an attacker to gain access to your remote servers. You must practice good security hygiene, including regularly updating your operating system and software, using a strong password manager, and avoiding clicking on suspicious links or opening untrusted attachments. By taking these measures, you significantly reduce the risk of your SSH connection being exploited.
In conclusion, SSH over the internet is an indispensable tool for anyone who requires secure remote access to their digital resources. Its strong encryption, versatile capabilities, and widespread availability make it an ideal solution for system administrators, developers, and anyone who values their privacy and data security. By understanding the principles behind SSH, implementing appropriate security measures, and leveraging its various features, you can create a robust and secure connection to your devices and data from anywhere in the world. From basic remote access to advanced tunneling and file transfer, SSH offers a wealth of functionalities that empower you to take control of your digital footprint. Remember, the key to successful SSH deployment lies not only in using the right tools but also in adopting a security-conscious approach to your digital life. Embrace the power of SSH and embark on a journey of secure and controlled access to your digital world.
| Key Concepts: | Secure Shell (SSH) |
| Definition: | A cryptographic network protocol used for secure data communication, remote login, and command execution. |
| Primary Function: | Provides a secure channel for accessing and managing remote systems over the internet. |
| Core Security Features: | Encryption (AES, RSA), authentication (key-based), integrity checks. |
| Key Use Cases: | Secure remote access, file transfer, port forwarding (tunneling), remote administration. |
| Prerequisites: | SSH server installed on remote device, SSH client on local device, internet connectivity. |
| Common Implementation Steps: | Enable SSH service, configure firewall rules (port forwarding if needed), configure SSH keys for authentication. |
| Security Best Practices: | Change default SSH port, disable password-based authentication, implement key-based authentication, regularly update server software, consider Fail2Ban or similar protection. |
| SSH Tunnels: | Local, remote, and dynamic port forwarding (SOCKS proxy) to bypass firewalls or access geo-restricted content. |
| File Transfer: | scp (secure copy) and sftp (Secure FTP), utilizing encryption and authentication. |
| Remote Administration: | Secure access for managing systems remotely, installing patches, and restarting services. |
| Challenges: | Firewalls, NAT, performance overhead (consider fast encryption algorithms like ChaCha20). |
| Additional Security: | Good local security (malware protection, strong passwords, up-to-date software). |
| Benefits: | Enhanced security, remote management, privacy protection, access to resources from anywhere with an internet connection. |
| Resources: | OpenSSH Official Website |